Defending Against Insider Threats to Security
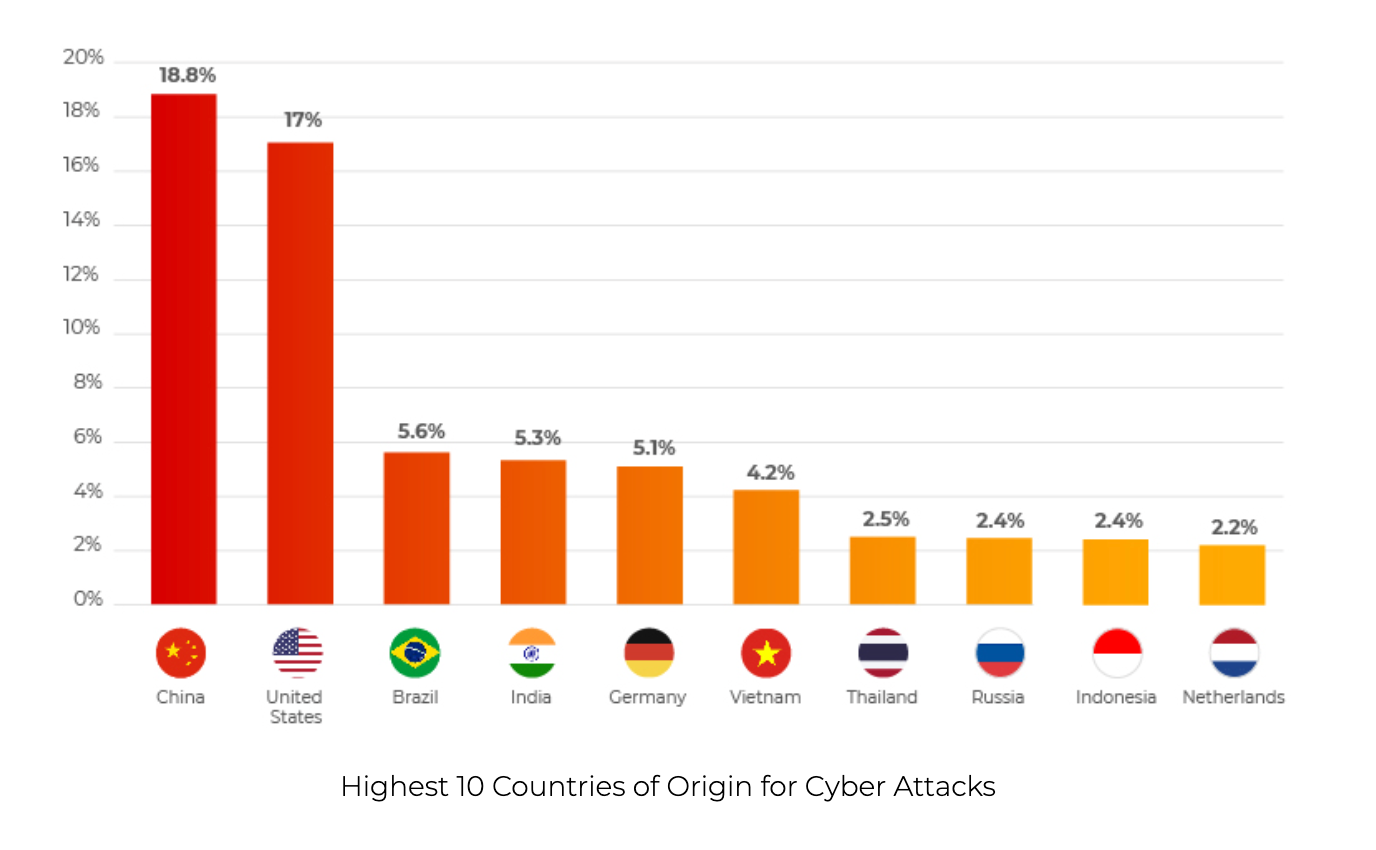
We often think about cybersecurity threats as originating from a dark basement or far away lands such as Russia or China. According to data from Cyberproof, China did indeed lead in attack originations in 2021 with 18.8% of all attacks followed closely by the United States at 17%. Russia represented only 2.4%.
Tracking the origins of foreign attacks can be difficult as hacked servers become staging grounds for new attacks blurring the true attack’s origin. But another attack vector that can be easier to track and far more damaging for the victims is insider attacks. Malicious and careless insiders are one of the key threats to corporate cyber security today. The 2021 Insider Threat Report by Cybersecurity Insiders, a 500,000-member community for information security professionals, reveals that 98% of organizations feel vulnerable to insider attacks. The Insider Threat Report data is based on the results of a comprehensive online survey of hundreds of cybersecurity professionals, conducted in January 2021. Other key takeaways from the report include:
- A majority of organizations (85%) consider unified visibility and control across all apps, devices, web destinations, on-premises resources, and infrastructure extremely to moderately important
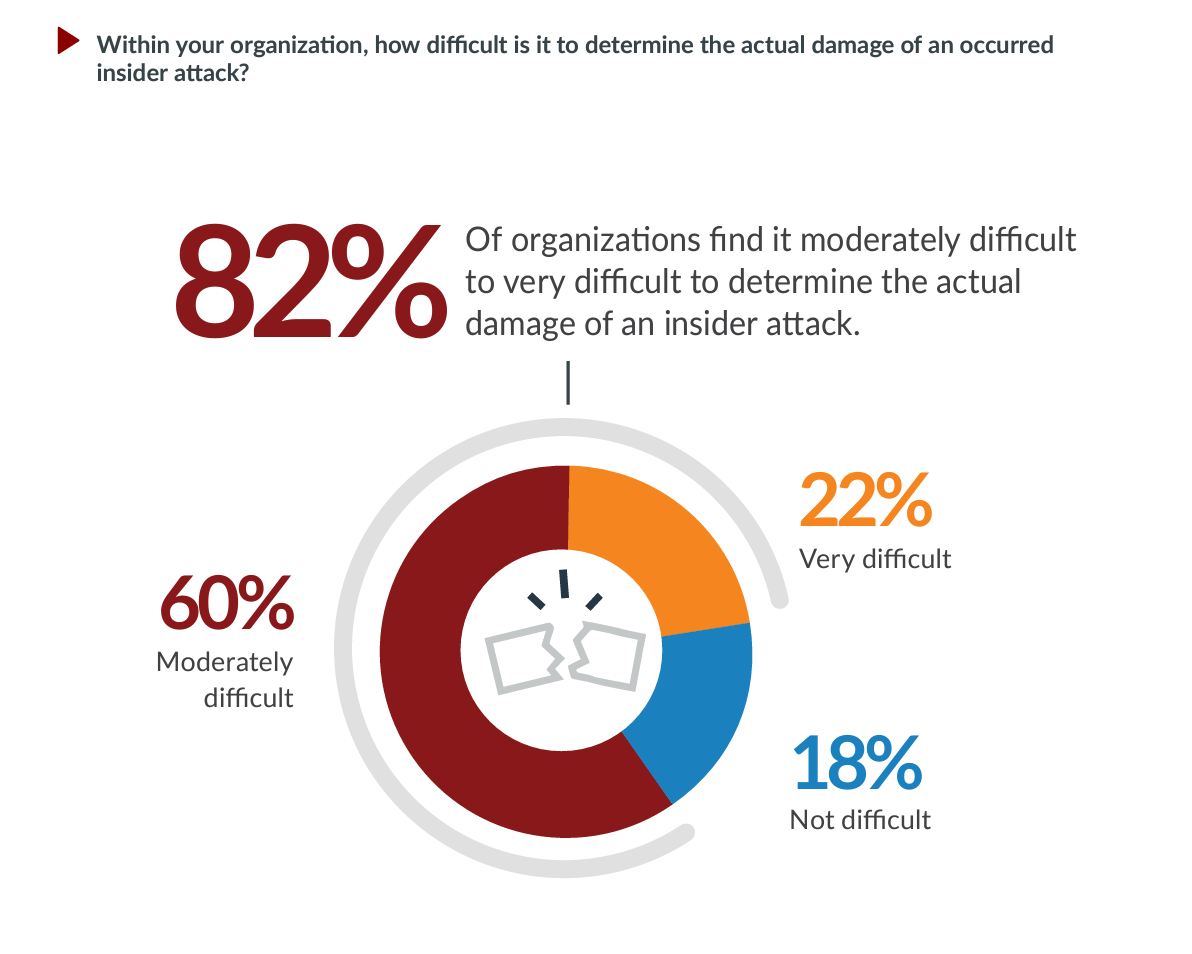
- 82% of organizations find it difficult to determine the actual damage of an insider attack
- 49% of organizations can’t detect insider threats or can only detect them after the data has left the organization
- Only 11% of organizations consider their monitoring, detecting, and response to insider threats extremely effective
Determining the effects and damage caused as a result of insider attacks can be difficult. Of the survey respondents, 82% stated it was moderately to very difficult to determine the actual damage caused by an insider attack.
The resulting impact of attacks can also be varied and costly. 40% of respondents listed critical data loss as the primary impact with operational disruption and brand damage rounding out the top three positions.

Along with the impacts revealed by the survey, organizations have also seen dramatic destruction in enterprise value as a result of high-profile insider attacks. Data collected by the Department of Justice states that in January 2021, the former cloud lead of Ubiquiti Networks stole the company’s confidential data by abusing his credentials for GitHub servers and Amazon Web Services. When working from home, Nickolas Sharp published a portion of stolen files and demanded a $2 million ransom from the company. After all the negative press coverage, the company’s market capitalization decreased by $4 billion as the stock price fell 20%. Just this past month another former Amazon Web Services employee was convicted of hacking into Capital One and stealing the data of more than 100 million people nearly three years ago in one of the largest data breaches in the United States.
The Cybersecurity & Infrastructure Security Agency further defines insider cyber threats as
The Department of Homeland Security National Cybersecurity and Communications Integration Center advises that “insider threats, to include sabotage, theft, espionage, fraud, and competitive advantage are often carried out through abusing access rights, theft of materials, and mishandling physical devices.” Threats can also result from employee carelessness or policy violations that allow system access to malicious outsiders. These activities typically persist over time, and occur in all types of work environments, ranging from private companies to government agencies.
The FBI has published a fact sheet listing recent high-profile insider attacks and the steps organizations can take to deter theft.
- Educate and regularly train employees on security or other protocols.
- Ensure that proprietary information is adequately, if not robustly, protected.
- Use appropriate screening processes to select new employees.
- Provide non-threatening, convenient ways for employees to report suspicions.
- Routinely monitor computer networks for suspicious activity.
- Ensure security (including computer network security) personnel have the tools they need
In addition to the FBI recommendations and strict human resources guidelines and monitoring of employees with high levels of access, transitioning to a zero-trust security environment could wind up saving your business.


![CISA Phishing Protection Recommendations [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph3ey82v3yws1xhe3qrjzci23y2f2zeozbzixdu.png)
