What Does A Cyber Security Analyst Do?
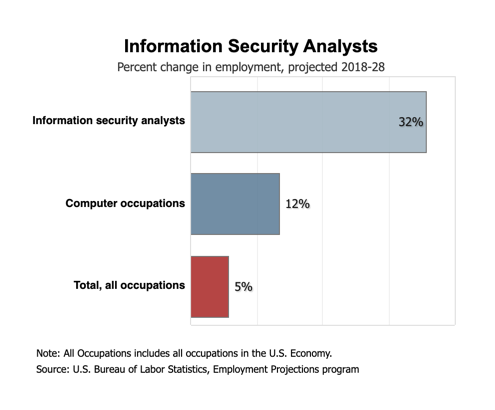
According to the Bureau of Labor Statistics (BLS), employment of cyber security analysts or information security analysts is projected to grow by 32% through 2028. This is due to the increasing utilization of the internet for the transmission and storage of sensitive data along with the increase in cyber threats worldwide.
A cybersecurity analyst’s main job functions include:
- Managing security policies
- Monitoring IT systems and networks for breaches or potential threats
- Updating IT systems to ensure policy compliance
- Educating teams on recent security trends, threats and compliance
The role of the Information Security Analyst is constantly changing and will continue to evolve as cyber threats increase. Currently, banks, governments, financial institutions and healthcare organizations lead the industries utilizing security analysts as they each strive to protect sensitive information, patient data and capital. However, the security analyst role continues to penetrate nearly all industries and organizations as identity theft, data breaches and wire fraud become more prevalent for all businesses.
Managing the security policy
The security analyst is responsible for not only managing the general security policy but may also be required to oversee network, server and application policies. A general security policy may also include sub-policies for:
- Acceptable Encryption Policy
- Acceptable Use Policy
- Clean Desk Policy
- Data Breach Response Policy
- Disaster Recovery Plan Policy
- Digital Signature Acceptance Policy
- Email Policy
- Ethics Policy
- Pandemic Response Planning Policy
- Password Construction Guidelines
- Password Protection Policy
- Security Response Plan Policy
- End-User Encryption Key Protection Policy
Policies document specific requirements that must be met by all users of the system. Along with overseeing the creation of the initial policies, the security analyst is also likely involved in the enforcement of the polices. In the case of a network security policy, this might also include:
- Acquisition Assessment Policy
- Bluetooth Baseline Requirements Policy
- Remote Access Policy
- Remote Access Tools Policy
- Router and Switch Security Policy
- Wireless Communication Policy
- Wireless Communication Standard
Knowing what policies are necessary and what requirements are needed in each policy is a significant portion of the security analysts’ role along with ensuring the policies remain up-to-date as systems change.
Monitoring IT systems and networks for breaches or potential threats
Whether in a cloud, hybrid or on-premise environment, a critical role of the security analyst is also to monitor the IT systems to identify breaches and real-time threats. When a potential breach or hacking attempt is discovered, the security analysts pulls in the appropriate teams to mitigate any loss or possible damage to system integrity. The analyst will commonly monitor software, hardware, and resource utilization. But unlike a systems analyst or database analyst who monitors for resource planning and performance, the security analyst is monitoring for signs of a potential breach or policy infringement.
Updating IT systems to ensure policy compliance
Policy updates not only help to mitigate risks as threats and systems change over time, but they also are required for policy compliance. Many organizations review policies annually or as needed when there are major changes in a business. Along with knowing what requirements to cover in a policy, a security analyst also helps to identify the appropriate policy review timeframe to ensure compliance.
Educating teams on recent security trends, threats and compliance
Sometimes the greatest threat to IT security is a culture problem more than an IT problem. If the CEO is lackadaisical towards security, a carelessness can easily trickle down throughout the organization. In many businesses, the security analyst is the one who is creating awareness and helping to shift the culture. This can be done through regular communications of recent threats and how they have negatively impacted other similar businesses. Often the best way to get a CEOs attention on a topic is to show how ignoring the topic can create a significant loss for the company. Many businesses have a schedule of regular security briefings where the cybersecurity team can present industry trends and heighten awareness throughout the organization. But often, the communication and education coming out of the security team is less formal and accomplished through timely emails or even a dedicated Slack channel.
The reason the BLS sees significant growth in Information Security over the coming years is quite clear. Security analysts play a critical role in protecting systems and data to ensure compliance, protect users and secure assets. Contact us to find out how a security analyst can help protect your business.



