Phishing SMS Attacks Accelerate Voice Attack Success
If you follow cyber security, you are likely all too familiar with the social engineering attack called phishing where an attacker sends a fraudulent message designed to trick a human victim into revealing sensitive information. We’ve written previously on how to spot these types of attacks as well as how to avoid them and how to educate your employees. Phishing has been around for decades and the traditional attack vector is through vast email campaigns with very low success rates. But even though the success rate is low, the attackers make these vast phishing campaigns work for them through large numbers. These traditional phishing attack methods are in direct contrast to spear-phishing or whaling attacks where high-profile targets such as CEOs are directly targeted.
Spear-phishing campaigns, with their more targeted nature, will even utilize voice phone calls initiated by real human beings to further lure the intended victim. When voice calls are used, the attacks are known as vishing or voice phishing. Other more widespread vishing campaigns will use automated dialers and text-to-speech synthesizers to cast a larger net. Vishing attacks will often make false claims of fraudulent activity on the victim’s bank accounts or credit cards and spoof the caller ID to look like the call originated from the impersonated bank or institution.
The attacker’s goal in all phishing campaigns is to extract information they can use in subsequent attacks or to advance the current attack. In traditional phishing campaigns, this is usually accomplished by directing the victim to a fraudulent web page made to look like a legitimate resource where information is collected or the user is tricked into downloading malware.
With the rise in SMS usage for multi-factor authentication and even banking transaction and fraud alerts, savvy attackers are leveraging this SMS familiarization and adding traditional text messaging to their attack platforms. The phrase “smishing” has been dubbed for use when SMS is used as the attack vector.
In a smishing campaign, the attackers may send out millions of text messages such as the example below to begin an interaction with potential victims. Any targets who respond to the SMS message will then receive a voice call that looks like it originated from the financial institution (J.P. Morgan Chase in this example).
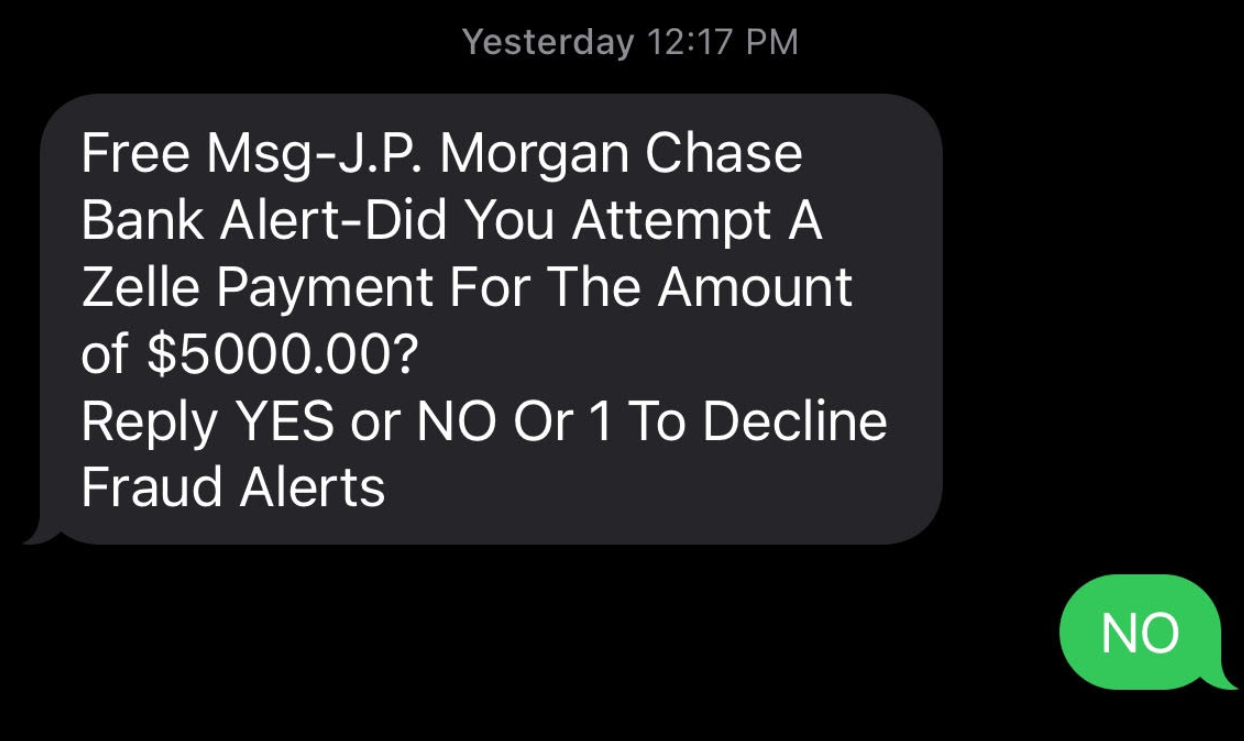
This combining of SMS messages along with voice call campaigns is finding a high success rate with targets because the process seems very legitimate. In some cases, the attackers are even calling the bank directly and impersonating the victim after the victim’s SMS response. This creates a contact record with the bank so a victim who calls the bank to confirm the contact is told the call was legitimate. And while the attackers have the victim on the phone, they may even send their own SMS verification code pretending to be part of the financial institution’s authentication process.
With the integration of SMS, voice, and email, phishing attackers are becoming very clever and also very successful in their scams. Some guidelines to help protect you and your employees from smishing and vishing are:
- Never trust caller ID for identification
- Only trust voice calls that you initiated to known or trusted phone numbers
- Don’t follow links sent via SMS
- Monitor and block suspicious outbound DNS requests
- Implement scanning to ensure malicious files don’t reach the network or endpoints
- Utilize sandboxing to detonate suspicious files
- Require multi-factor authentication



