Defending Against Advanced Persistent Threats APT
We reported on the highly sophisticated FireEye breach last December. In the attack, the criminals targeted and accessed certain FireEye Red Team assessment tools which are used to mimic the behavior of many cyber threat actors and provide diagnostic security services to FireEye’s customers. The breach was investigated by the FBI, Microsoft as well as FireEye analysts. During the investigation, it was discovered the breach on FireEye was part of a much larger attack carried out through an update service from the Austin Texas-based IT Management and Software company Solarwinds. The attack on FireEye quickly moved into the background as the much larger SolarWinds attack was revealed and consumed the headlines. The attack on SolarWinds was novel and utilized a combination of techniques not seen before. The hack would become known as one of the most sophisticated and large-scale cyber operations ever identified. It affected federal agencies, courts, numerous private sector companies, and state and local governments across the country. The attack was identified as a supply chain attack because of the way the malicious code was distributed through SolarWinds to their customers creating a network effect. Leveraging a supply chain certainly gave the SolarWinds attack its historic scale. But what could be seen as more impressive, was the attacker’s ability to remain undetected within SolarWinds resources for an extended period.
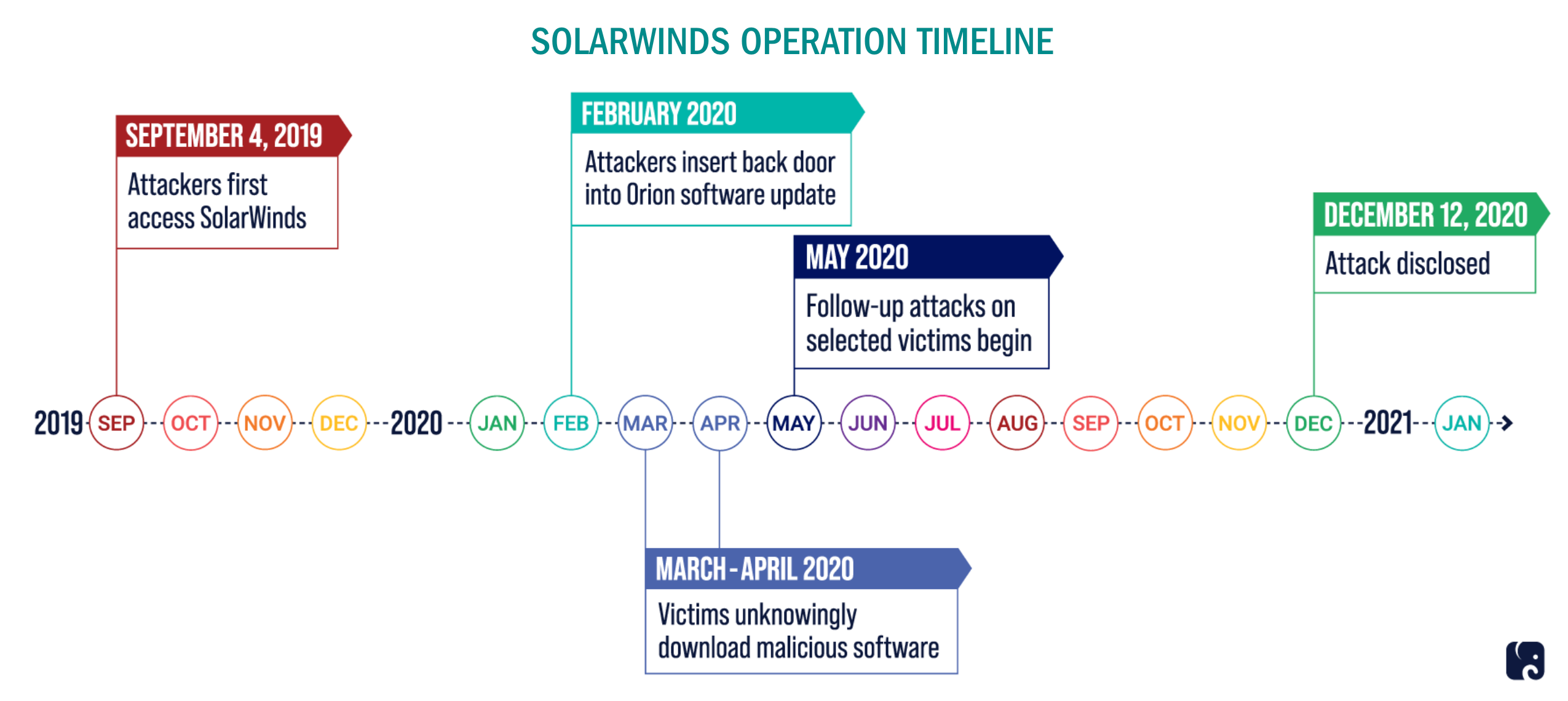
According to the Department of Homeland security, the SolarWinds attackers remained hidden within SolarWinds networks for over 12 months. Attacks with this sophistication and duration are known as Advanced Persistent Threats or APT. The NIST defines APT as.
An adversary with sophisticated levels of expertise and significant resources, allowing it through the use of multiple different attack vectors (e.g., cyber, physical, and deception) to generate opportunities to achieve its objectives, which are typically to establish and extend footholds within the information technology infrastructure of organizations for purposes of continually exfiltrating information and/or to undermine or impede critical aspects of a mission, program, or organization, or place itself in a position to do so in the future; moreover, the advanced persistent threat pursues its objectives repeatedly over an extended period of time, adapting to a defender’s efforts to resist it, and with determination to maintain the level of interaction needed to execute its objectives.
APT attacks have more serious consequences than conventional attacks because the victims tend to be higher profile. If the attackers are going to invest significant time and resources for an APT, it’s generally for a more significant target. An example being the APT attack on Microsoft Exchange servers last January that affected over 250,000 servers around the world and breaches of over 30,000 US entities. But just because the initial focus of the APT is a high-profile target, that doesn’t mean small and mid-sized organizations are safe. As with both the SolarWinds and Microsoft attacks, the initial target is large but the resulting victims include groups of all sizes.
Solutions such as WatchGuard’s APT Blocker allow for defending against APT attacks by employing an isolated sandbox in the Cloud which simulates the behavior of physical hardware. This allows for analyzing all types of executables and documents in a safe environment before they infect the targeted network. Using APT Blocker, even zero-day threats can be neutralized without risk.
By adding Endpoint Protection, Detection, and Response (EPDR) to your security array, you can employ a zero-trust strategy along with integrated threat hunting. This allows for every binary entering your network to be thoroughly analyzed before you become the next victim. WatchGuard EPDR is an innovative cybersecurity solution for laptops, computers, and servers that combines the widest range of endpoint protection (EPP) technologies with EDR capabilities. It protects users from advanced threats, APTs, zero-day malware, ransomware, phishing, rootkits, in-memory exploits, and malware-less attacks, and also provides IDS, firewall, device control, and URL & content filtering capabilities. EPDR uniquely automates the prevention, detection, containment, and response actions for ultimate security that is easy to manage and deploy. Contact us to learn more about how to employ advanced techniques like these to keep your data and systems safe.


![CISA Phishing Protection Recommendations [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph3ey82v3yws1xhe3qrjzci23y2f2zeozbzixdu.png)
