Defending Against the Human Vulnerability in Cyber Attacks
In the world of cybersecurity, our conversations often center around defending against attack strategies such as phishing or monitoring attack trends such as ransomware. But in the end, ransomware only becomes ransomware when the attackers decide to monetize the breach through a ransom demand. Analyzing the origin of the breach is far more informative to prevention than the hacker’s demand of ransom. While million-dollar ransoms make great headlines, each of those ransoms likely started with either a credential attack, phishing attack, or exploiting a system vulnerability. And defending against these attacks means plugging those vulnerabilities. According to Verizon’s 2022 Data Breach Investigations Report, over 80% of attacks exploited one of these attack vectors.
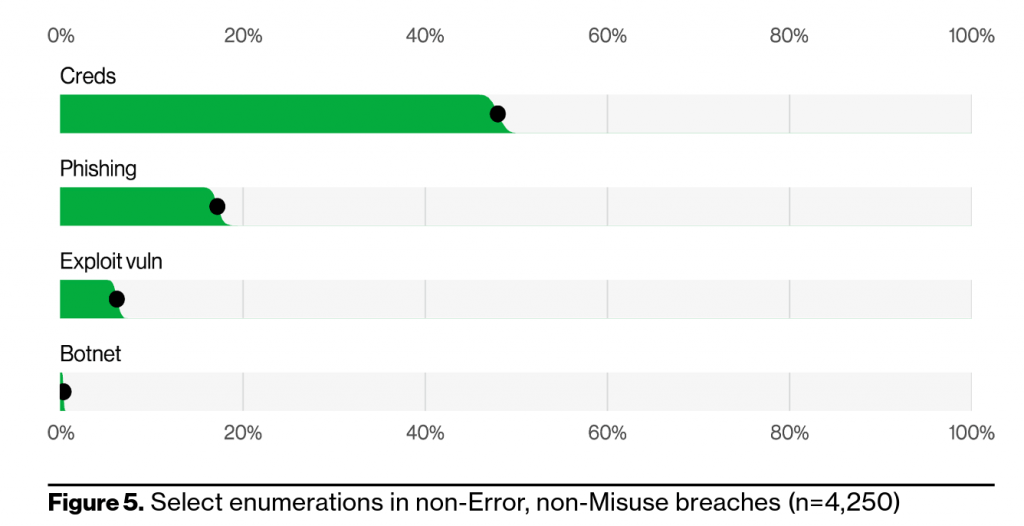
The common denominator in each of these frequently exploited attack paths is the human element. Humans choose weak credentials, reuse credentials, or store and transmit credentials insecurely. Humans fall victim to phishing attacks and reveal personal or corporate sensitive information. And humans make up the system administrators who misconfigure applications or don’t patch systems allowing for easy exploitation of vulnerabilities that could have easily been secured. Defending against attacks becomes exponentially more difficult when employees are leaving the front door open.
The human element continues to drive breaches. This year 82% of breaches involved the human element. Whether it is the Use of stolen credentials, Phishing, Misuse, or simply an Error, people continue to play a very large role in incidents and breaches alike.
— Verizon 2022 DBIR
Protecting against our human vulnerabilities requires a proactive approach to segmenting our data and systems — cordoning off information so a breach in one area can’t move laterally across our system. If we assume someone will eventually leave the front door open, we want to make it difficult for an intruder to move freely from office to office.
It requires explicit verification and authorization of users based on all data available including the device used, location, the services, and hardware-bound multi-factor authentication (MFA) to eliminate credential attacks. Users should not be able to log in from multiple locations easily. If an employee was logged in from the office in Minneapolis this afternoon are they really trying to log in from Russia in the evening?
It requires limiting user access based on the principle of least privilege to only allow access to what they need to complete a given task in a pre-determined amount of time. If a low-privilege user falls victim to a phishing attack, you should be able to rest assured their access level did not give up information allowing for a further attack.
And it requires creating an internal mindset to accept the reality that your organization is likely under attack every minute of every day. Assume a breach is happening and actively monitor your environment to protect against the ongoing threat. Employees and vendors should feel comfortable reporting unusual activity without second-guessing their decision. And they should know exactly how to report the activity because they have been trained to be on guard. This mindset is encapsulated by adopting a zero-trust security model.
If we know our systems are under attack and we know the human element is our greatest weakness, we proactively prepare for the eventual breach through data protection, secure backups, and a breach response plan to restore critical systems. This includes:
- Implement automated backups of all critical systems and regularly test backup integrity.
- Protect backups from inclusion in a system breach.
- Regularly test your breach response and disaster recovery plans and separately protect these plans from inclusion in a breach
Defending against the human element is an added challenge to any security plan but the right training, configurations, and security policies will harden your systems to attack. An ounce of prevention could be worth avoiding millions in ransom.



