Detecting Insider Threats to Security
Discussions around IT security generally center on software, budgets, virtual infrastructure, firewalls, backups, and user credentials. Often missing from the conversation is the human component and insider threats to security. We all want to believe our employees, vendors, consultants, business partners, and even board members are trustworthy, but the truth is that today’s most damaging security threats don’t originate from outsiders or malware but from trusted insiders. According to a CA Insider Threat Report from 2018, over 50 percent of organizations suffered an insider threat-based attack in the prior 12 months, while a quarter reported suffering attacks more frequently than in the previous year.
Not all insider threats are intended to do harm. Often the vulnerabilities derive from human negligence or simply circumventing security because it makes the job easier. According to research from Cyber Security Insider, 63% of organizations think that privileged IT users pose the biggest insider security risk to organizations.
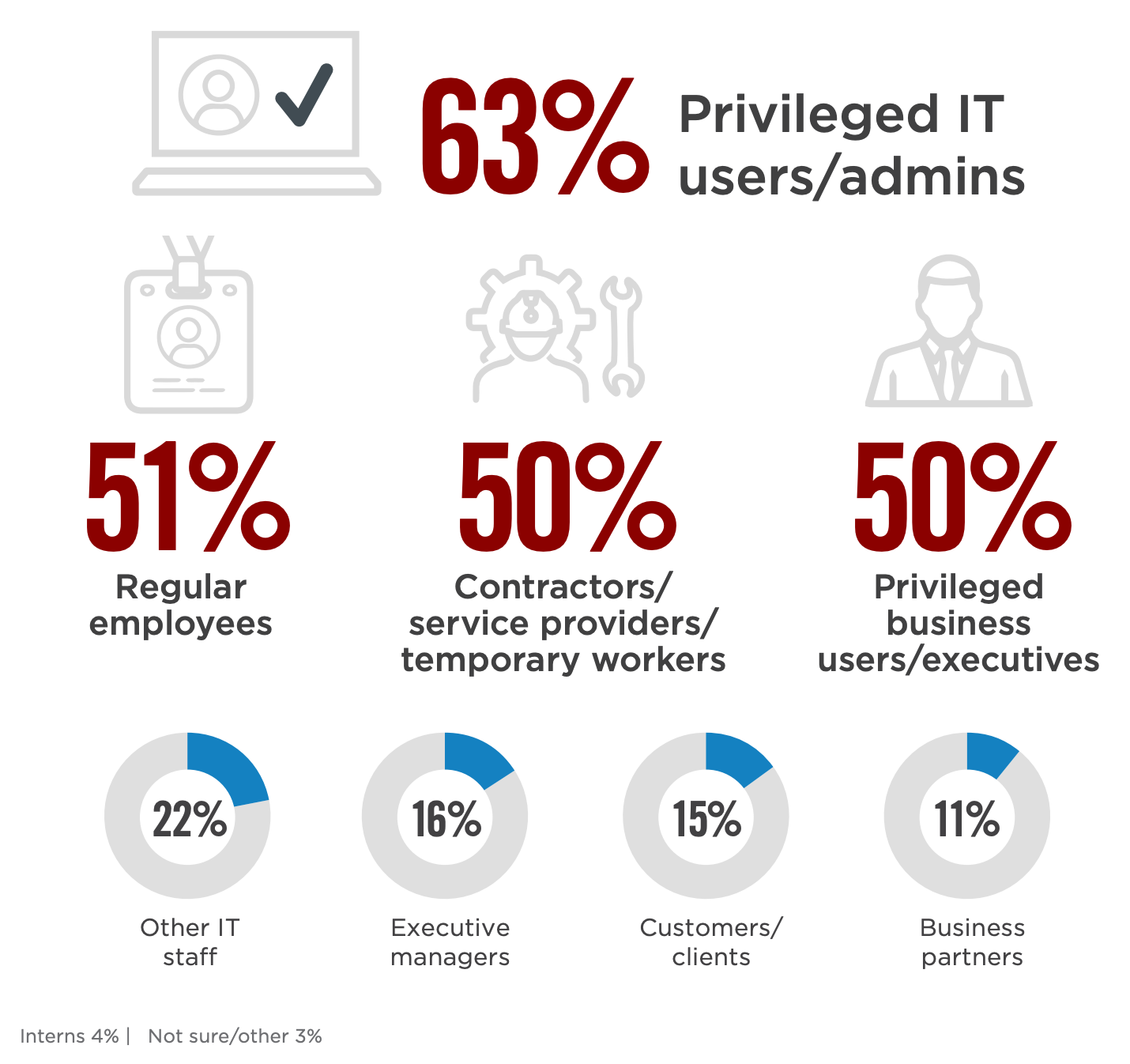
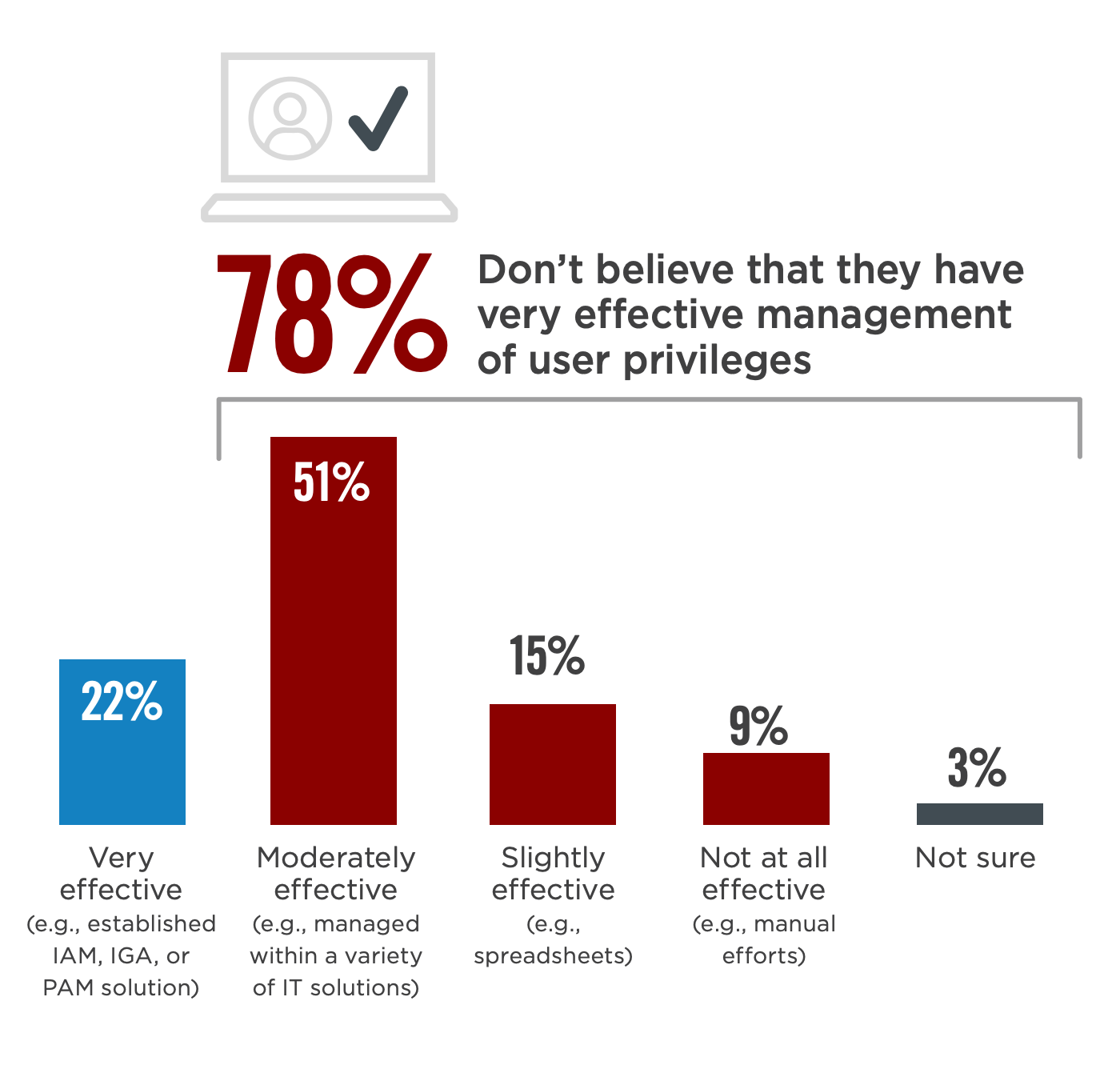
And 78% of businesses surveyed don’t believe they have very effective management of user privileges. Insider threats present another layer of complexity for IT professionals to manage, requiring careful planning with regards to access controls, user permissions, and monitoring user actions.
In 2020, we witnessed insider threats play out at the likes of Amazon as a former Finance Manager was charged in a $1.4 million insider trading scheme, an insider attack at Stradis Healthcare as a former VP Finance carried out an attack that disrupted the delivery of personal protective equipment, and a data breach at Shopify as two employees stole merchant information.
Recently, Shopify became aware of an incident involving the data of less than 200 merchants. We immediately launched an investigation to identify the issue–and impact–so we could take action and notify the affected merchants.
Our investigation determined that two rogue members of our support team were engaged in a scheme to obtain customer transactional records of certain merchants. We immediately terminated these individuals’ access to our Shopify network and referred the incident to law enforcement. We are currently working with the FBI and other international agencies in their investigation of these criminal acts. While we do not have evidence of the data being utilized, we are in the early stages of the investigation and will be updating affected merchants as relevant.
Source: Shopify Blog
The key to preventing insider threats is to identify the warning signs to stop an attack or breach before it happens. A critical component of creating a risk profile identifying potential insider threats is knowing who the likely perpetrators are, what data they may be targeting, and why. This will enable you to put greater restrictions on potential threat actors and more controls on vulnerable data. Some behavioral signs to watch out for include:
- Using unauthorized devices
- Searching for sensitive data or network crawling
- Accessing data not associated with their job function
- Data hoarding or copying sensitive files
- Emailing sensitive data outside the organization
- Any attempt to bypass security
- Frequent off-hours office use
- Displaying disgruntled behavior
- Violations of other corporate policies
- Discussions of resigning or other employment opportunities
Identifying these warning signs early can help minimize internal risks by enabling you to detect, investigate, and act on malicious and inadvertent activities in your organization. Establishing insider risk policies allow your organization to define the types of risks to identify, and detect in your organization, including acting on cases and escalating cases as appropriate. Established policies may include:
- Data theft by departing users
- General data leaks
- Data leaks by priority users
- Data leaks by disgruntled users
- General security policy violations
- Security policy violations by departing users
- Security policy violations by priority users
- Security policy violations by disgruntled users
Users in the modern workplace have access to create, manage, and share data across a broad spectrum of platforms and services. In most cases, organizations have limited resources and tools to identify and mitigate organization-wide risks while also meeting user privacy standards. The threat exists in all organizations large and small. This year Tesla CEO Elson Musk said an insider was found making “direct code changes to the Tesla Manufacturing Operating System under false usernames and exporting large amounts of highly sensitive data to unknown third parties.”
If you are ready to protect your data from insider threats, we can help audit your current environment as well as implement and manage appropriate policies, data loss prevention (DLP), encryption at rest, identity and access management (IAM), behavioral analytics, tailored log and event management, along with other strategies to keep you from being the next victim and maintain compliance with HIPAA or PIC information security requirements.



