Health and Human Services Ransomware Trends 2021
It’s no secret that ransomware attacks are on the rise. According to a Department of Health and Human Services Ransomware Trends 2021 report:
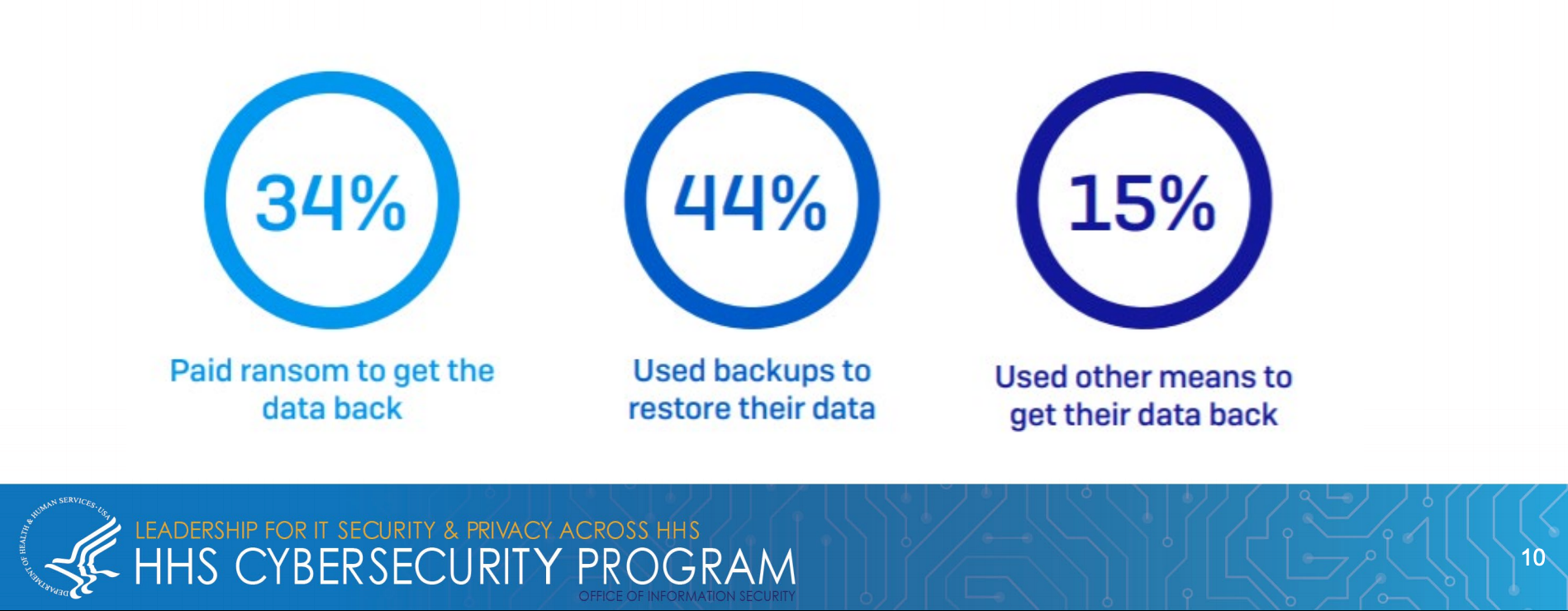
- 34% of healthcare organizations were hit by ransomware in the last year.
- 65% that were hit by ransomware in the last year said the cybercriminals succeeded in encrypting their data in the most significant attack.
- 44% of those whose data was encrypted, used backups to restore their data.
- 34% of those whose data was encrypted, paid the ransom to get their data back in the most significant ransomware attack.
- 93% of affected HPH organizations got their data back, but only 69% of the encrypted data was restored after the ransom was paid.
Since the attackers are getting paid, the trend is showing the attacks are not going to slow down.
“I don’t think that what we are seeing from a rise in volume perspective is going to shift anytime soon. After all this market is now a $1.5 trillion market according to the World Economic Forum. So if I’m an attacker, why would I slow down. I’m getting the ROI that I want. I’m getting those extorsions paid.”
Those are the words of Rick McElroy, Principal Cybersecurity Strategist for VMware, in a recent interview. McElroy goes on to explain that the urgency of receiving information such as medical and vaccine news centered around the pandemic created a ripe environment for criminals to take advantage of users through spear-phishing. He also points to the expanding attack surface as on-premise security solutions broke down as a global workforce transitioned to work-from-anywhere.
In many ways, cyberattacks have become a new pandemic bolted on top of the viral pandemic. McElroy’s statement on attackers’ ROI has proven true time and again. Every week we hear of new organizations being attacked and paying out millions such as the recent CNA Financial Corp. $40 million payout in late March or the highly publicized Colonial Pipeline $4.4 million payment in May. The FBI has historically discouraged but not prohibited American ransomware victims from paying their attackers.
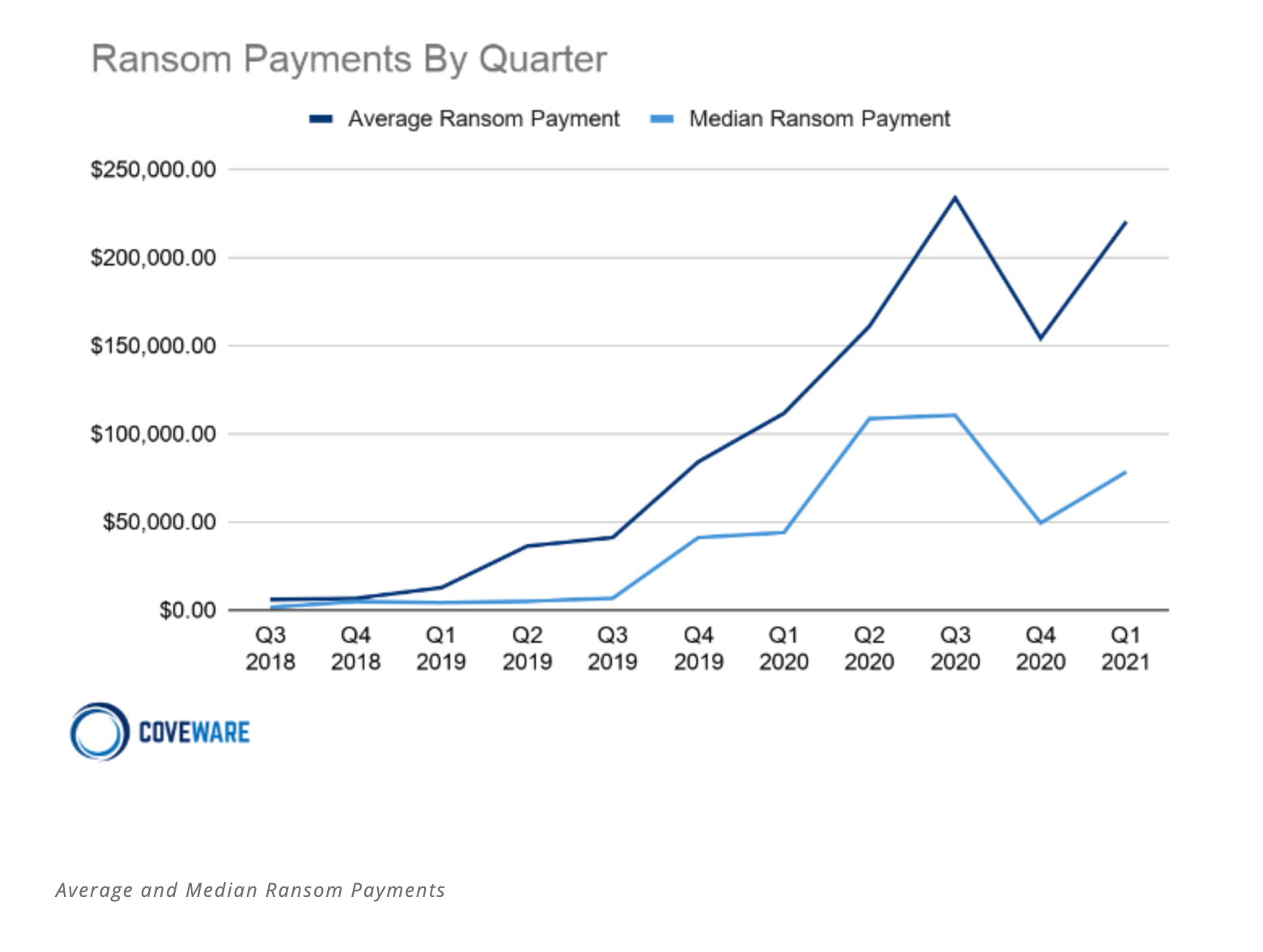
The unfortunate reality is that many businesses end up paying the ransoms because they didn’t take proper preventative security and resiliency measures. In many cases, when discussing IT budgets and security, corporate boards and executives are not properly allocating dollars towards prevention and risk mitigation. Instead of budgeting for resiliency, they are paying out hundreds of thousands to millions in order to resume operations. According to Coveware’s Q1 2021 Ransomware Report, average ransomware payments increased by 43% from Q4 2020 to an average of $220,298.
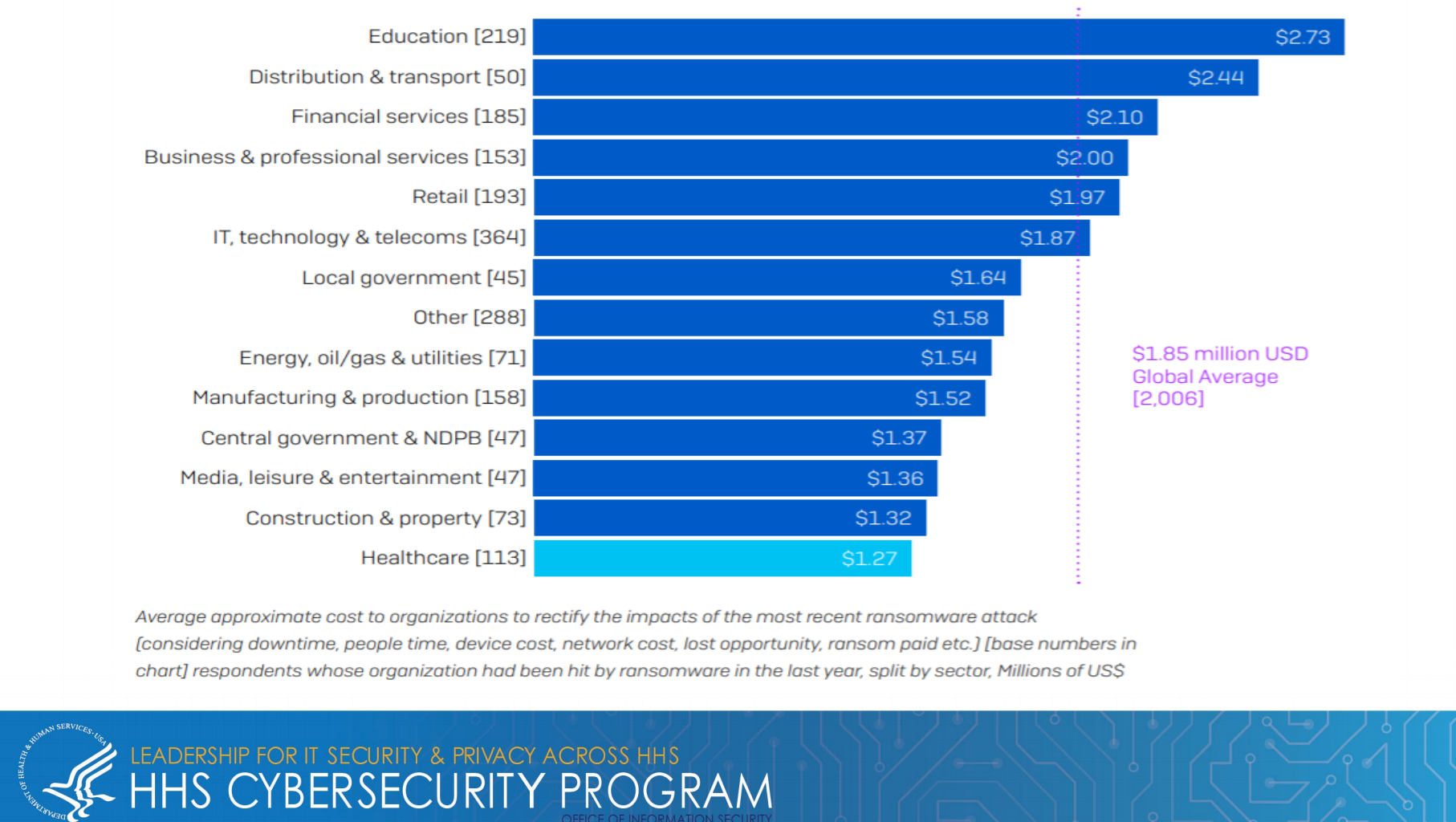
We are even hearing cases of companies keeping bitcoin on their balance sheets so they have liquidity and are ready to pay the ransom if they are attacked. According to the Health and Human Services report, the average ransomware cost per incident was $1.85 million — considering downtime, people time, device cost, network cost, lost opportunity, ransom paid, etc. With education being the hardest hit at $2.73 million average incident cost.
Cybersecurity & Infrastructure Security Agency (CISA) Recommendations to prevent business disruption from a ransomware attack include:
- Require multi-factor authentication for remote access to OT and IT networks.
- Enable strong spam filters to prevent phishing emails from reaching end users. Filter emails containing executable files from reaching end users.
- Implement a user training program and simulated attacks for spear phishing to discourage users from visiting malicious websites or opening malicious attachments, and re-enforce the appropriate user responses to spear-phishing emails.
- Filter network traffic to prohibit ingress and egress communications with known malicious IP addresses. Prevent users from accessing malicious websites by implementing URL blocklists and/or allow lists.
- Update software, including operating systems, applications, and firmware on IT network assets, in a timely manner. Consider using a centralized patch management system; use a risk-based assessment strategy to determine which OT network assets and zones should participate in the patch management program
- Limit access to resources over networks, especially by restricting RDP. After assessing risks, if RDP is deemed operationally necessary, restrict the originating sources and require multi-factor authentication.
- Set anti-virus/anti-malware programs to conduct regular scans of IT network assets using up-to-date signatures. Use a risk-based asset inventory strategy to determine how OT network assets are identified and evaluated for the presence of malware.
- Implement unauthorized execution prevention by:
- Disabling macro scripts from Microsoft Office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full Microsoft Office suite applications.
- Implementing application allow-listing, which only allows systems to execute programs known and permitted by security policy.
- Monitor and/or block inbound connections from Tor exit nodes and other anonymization services.
- Deploy signatures to detect and/or block inbound connections from Cobalt Strike servers and other post-exploitation tools.


![CISA Phishing Protection Recommendations [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph3ey82v3yws1xhe3qrjzci23y2f2zeozbzixdu.png)
