NIST Updated Cybersecurity Guidance for U.S. Manufacturers
The National Institute of Standards and Technologies (NIST) develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies, and the broader public. Their activities range from producing specific information that organizations can put into practice immediately to longer-term research that anticipates advances in technologies and future challenges.
The NIST has recently updated its cybersecurity guidance for U.S. manufacturers and supply chain risks. Supply chain attacks targeting manufacturers and distributors remain a weak link in our nation’s commerce and have given rise to the largest attacks in history. The ability of cyber criminals to propagate their attacks via vendor access to networks and systems has exponentially increased the breadth of recent incidents. Similar to the network effect in social networking, when an attacker targets a supply chain, they can gain access to hundreds or thousands of down-chain systems through one attack. Common security measures focus on employees, firewalls, multi-factor authentication, software updates, and endpoint protection but 3rd party vendor access is often less secure simply because of less visibility and control over vendors. This is especially true when the attack spreads through a trusted software update as seen in the Solar Winds attack.
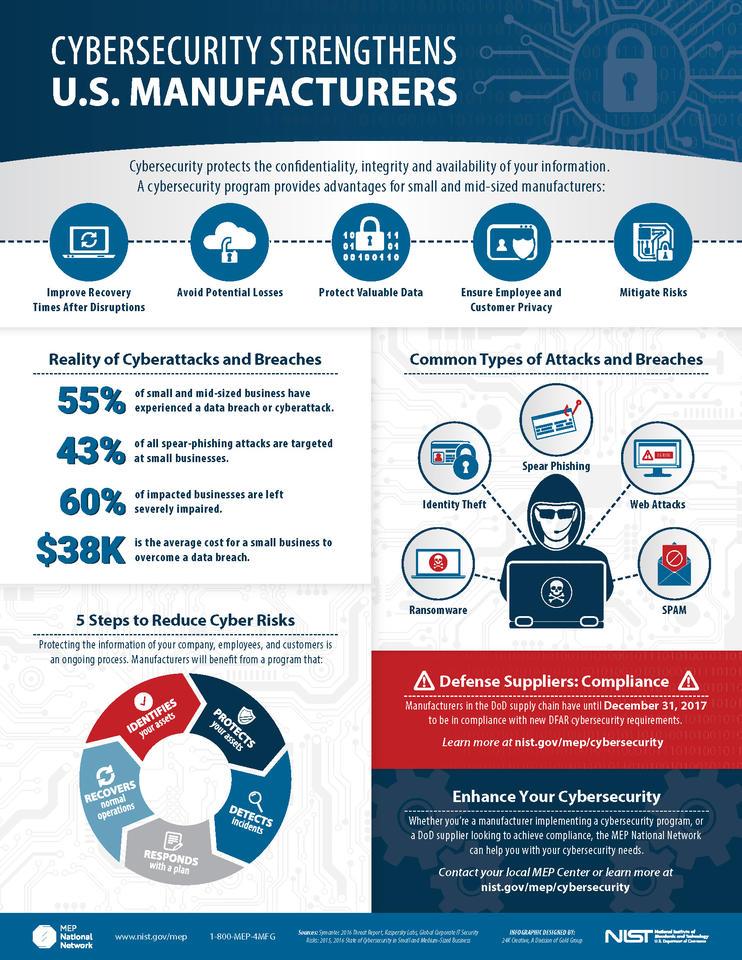
Today’s global commerce relies heavily on supply chains that connect our worldwide network of manufacturers, distributors, software developers, and service providers. The same network that empowers our economy can also bring it to its knees. Vendor access to these systems through user accounts and manufactured component access in finished products should be scrutinized and monitored with stringent security tools and policies. A device may have been designed in one country and built in another using multiple components from various regions of the world that have themselves been assembled from parts originating through disparate manufacturers. A recent example is the network routers sold at Amazon, eBay, and Walmart that included a malicious backdoor. Not only might the resulting product contain malicious software or be susceptible to cyberattack, but the vulnerability of the supply chain itself can affect a company’s bottom line through downtime, remediation, or even liability.
“A manufacturer might experience a supply disruption for critical manufacturing components due to a ransomware attack at one of its suppliers, or a retail chain might experience a data breach because the company that maintains its air conditioning systems has access to the store’s data sharing portal,”
Jon Boyens – NIST
The updated NIST guidance and the full list of recommended security controls can be found here. It is a beneficial read for cybersecurity specialists, risk managers, systems engineers, and procurement officials. The full guidance covers topics including:
- Access Control
- Awareness and Training
- Audit and Accountability
- Assessment, Authorization, and Monitoring
- Configuration Management
- Contingency Planning
- Identification and Authorization
- Incident Response
- Maintenance
- Media Protection
- Physical and Environmental Protection
- Planning
- Program Management
- Personnel Security
- Personally Identifiable Information Processing and Transparency
- Risk Assessment
The updated guidance is extensive and the NIST plans to publish a quickstart guide in the near future to help organizations begin the process of implementing controls.



