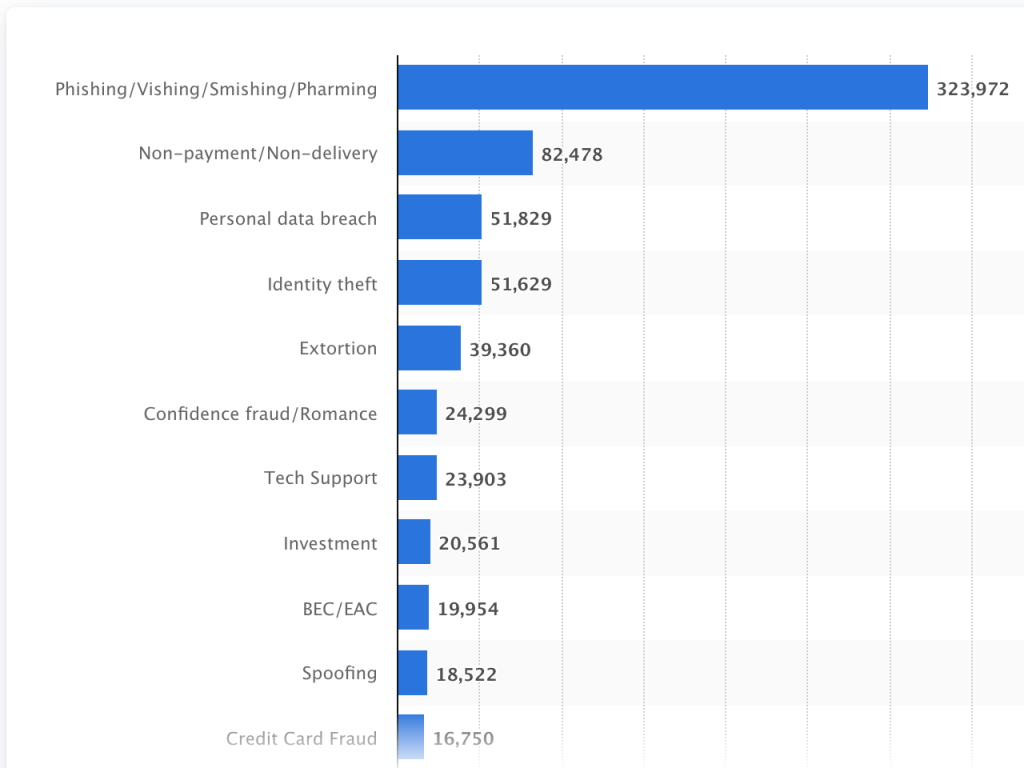
SMS Phishing aka Smishing Attacks on the Rise
Although the term “smishing” was originally coined in 2016, the “SMS + phishing” identifier remains relatively unknown to the general public. According to data from Proofpoint, a security company that processes more than 80% of America’s mobile messages, only 23% of users over the age of 55 were aware of the term. And Millenials didn’t fare much better with only 34% recognition. Despite this, smishing attacks were the most commonly reported type of cyberattack in 2021 as reported to the U.S. Internet Crime Complaint Center and Statistia,
Smishing or SMS phishing is an attempt by an attacker to trick users into revealing personal information via mobile messaging. The information the attackers are targeting can be a social security number, a credit card number, or health insurance information but is often simply a one-time password or OTP to circumvent an SMS-based multi-factor authentication implementation.
As seen in the smishing example below provided by Cloudflare, the attackers use an official-looking domain name including the attack target company name along with the familiar Okta authentication service. In the case of the recent attack on Cloudflare, the domain had only been registered 40 minutes before the attack began. By coordinating the domain registration and immediate broadcasting of the smishing campaign, attackers are able to complete the assault before the domains were blacklisted by alerting services.
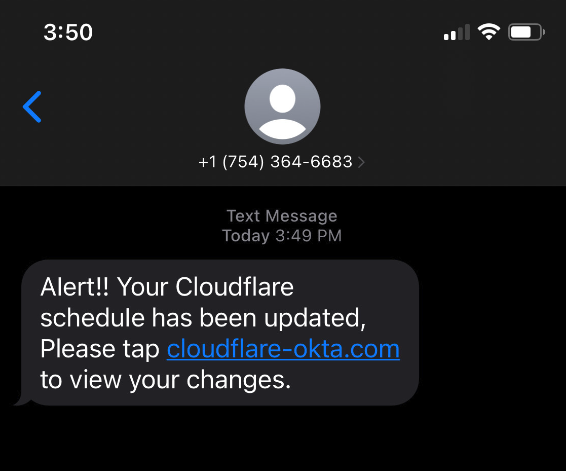
These attacks are implemented with simple tools and allow criminals to interact directly with employees of even the largest enterprises. And the attacks are working.
As Cloudflare disclosed on their blog after revealing the attack, employees who clicked the smishing link were sent to a replica login page, seen below, that also appeared official.
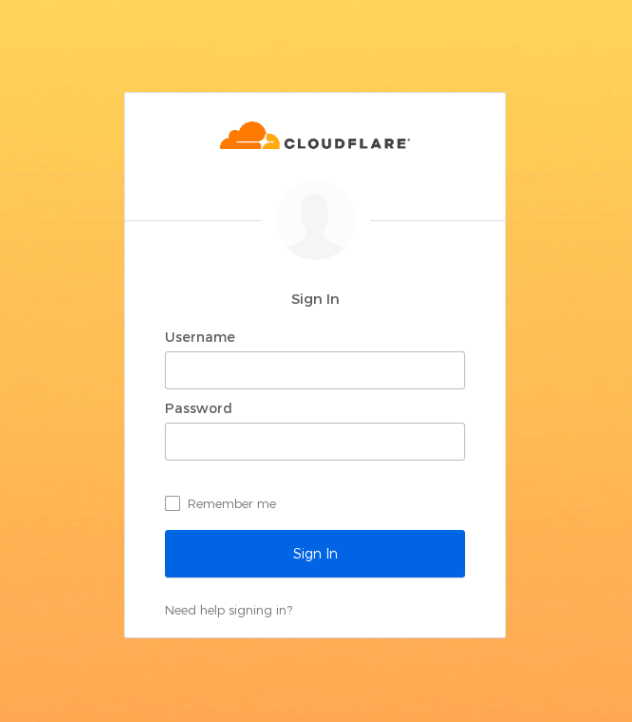
When credentials were entered on the page, they were immediately sent to the attackers in real time via Telegram. The phishing page then asked for the OTP code which was also immediately forwarded to the attackers completing the criminal authentication. Despite high levels of training and awareness at Cloudflare, a total of 3 employees fell for the attack. A total of 76 employees were targeted and over 90% reported the attack to the Cloudflare Security Incident Response Team (SIRT) as suspicious.
Even though some Cloudflare employees fell victim, no breach was realized because Cloudflare does not use SMS-based OTP in their MFA implementation. Instead, every employee is issued a FIDO2-compliant security key similar to those available with AuthPoint.
In many cases, the smishing campaigns are just the beginning of the attack. Based on research from Group-IB, the attackers subsequently targeted mailing lists and customer-facing systems in order to launch supply chain attacks.
- Marketing firm Klaviyo was breached and personal information connected to cryptocurrency-related accounts, reportedly including names, addresses, emails, and phone numbers, was stolen. This information could be used in order to steal cryptocurrency.
- Email platform Mailchimp was breached to gain access to data from crypto-related companies and disrupt operations. Mailchimp was used by technology firm DigitalOcean to send confirmation emails, password resets, email-based alerts. By initiating and redirecting password resets the customers of DigitalOcean could have been compromised.
- Phone number verification provider Twilio was breached, which allowed the attacker to attempt to re-register Signal accounts to new mobile devices.
Technology alone can’t protect users from all social engineering attacks. In the Cloudflare example above, employees were highly trained to be suspicious and report anything unusual. Awareness and training are critical lines of defense against these attacks. Of course, properly implemented hardware-based MFA and zero-trust security policies are necessary but here are some recommendations on how to keep your team safe.
- All users should verify the URLs where they are entering credentials — especially administrative and privileged users.
- Establish FIDO2-compliant MFA like WatchGuard AuthPoint
- Report anything suspicious to the appropriate channels. And have established reporting protocols in place and employees trained.
- Keep your head on a swivel, unfortunately corporate employees are the prey



