9 Steps to Fight the Evolving Threat from Phishing Attacks
Phishing attacks, the act of tricking or luring targets into revealing sensitive information, remain a substantial threat to businesses and are increasing in frequency. According to new data from Microsoft in their 2022 Digital Defense Report, phishing attack volume is more than ten times greater than all other attacks. Microsoft also found that after a successful phishing email, an attacker has already accessed your critical data within 1 hour and 12 minutes and 30 minutes later has begun moving laterally throughout your corporate network. Email phishing or Business Email Compromise (BEC), according to Microsoft, is the costliest financial cybercrime, with an estimated $2.4 billion USD in adjusted losses in 2021, representing more than 59% of the top five internet crime losses globally.
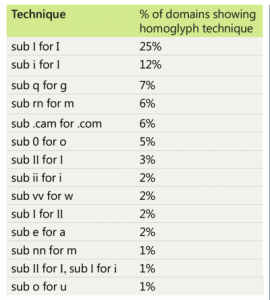
Phishing attacks and BEC continue to grow in complexity as they adapt to circumvent the latest defenses. In 2022, homoglyphs remained a key component of many phishing attacks. A homoglyph is where an attacker substitutes a character in a well-recognized domain name with a similarly appearing character to trick the user into thinking the domain or URL is legitimate. The table below represents an analysis by Microsoft of over 1,700 homoglyph domains between January–July 2022. While 170 homoglyph techniques were used overall, 75% of offending domains used just 14 primary techniques below.
But phishing attacks are also evolving beyond the use of homoglyphs in order to fool their targets. Today advanced attacks are leveraging compromised aspects of trusted services so the criminals can avoid purchasing, hosting, and operating their own spoof domains. This helps attackers avoid detection, extend a campaign’s lifetime, and improve overall campaign results. Attackers are relying on previously compromised email accounts and domains with high reputation scores to ensure a higher delivery and success rate in attacks. Leveraging pre-existing trusted accounts avoids the easier filtering by defense systems of newly created and untrusted accounts. For example, Microsoft found attackers preferred to send and spoof from domains with DMARC incorrectly configured with a “no action” policy allowing easier email spoofing. Attackers would also leverage cloud services and cloud virtual machines (VMs) to fully automate campaigns from VM SMTP relays to benefit from high deliverability rates and strong reputation scores.
Organizations looking to reduce their exposure to phishing attacks are strongly encouraged to implement the following policies and features.
- Require the use of MFA across all accounts to limit unauthorized access.
- Enable conditional access features for highly privileged accounts to block access from countries, regions, and IPs that do not typically generate traffic at your organization.
- Consider using physical security keys for executives, employees involved in payment or purchase activities, and other privileged accounts.
- Enforce the use of browsers that support services such as Microsoft SmartScreen to analyze URLs for suspicious behaviors and block access to known malicious websites.
- Use a machine-learning-based security solution that quarantines high-probability phish and detonates URLs and attachments in a sandbox before the email reaches the inbox, such as Microsoft Defender for Office 365.
- Enable impersonation and spoofing protection features across your organization.
- Configure DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication Reporting & Conformance (DMARC) action policies to prevent delivery of non-authenticated emails that might be spoofing reputable senders.
- Audit tenant and user-created allow rules and remove broad domain and IP-based exceptions. These rules often take precedence and can allow known malicious emails through email filtering.
- Regularly run phishing simulators to gauge the potential risk across your organization and to identify and educate vulnerable users.


![CISA Phishing Protection Recommendations [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph3ey82v3yws1xhe3qrjzci23y2f2zeozbzixdu.png)
