The Growing Threat from Ransomware
Last month, Garmin Ltd., the GPS device and service provider, confirmed the worldwide outage of their network due to a cyber attack. The attack turned out to be a ransomware attack using a new, highly adaptable ransomware strain called WastedLocker tied to Russia’s Evil Corp malware dynasty. A few weeks later Tesla Inc reported an attempted ransomware attack that could have been devastating to the electric car and solar manufacturer,
Luckily for Tesla, the attack was thwarted due to an extremely loyal employee who turned down a $1 million bribe to install malware on Testa’s Gigafactory network in Nevada. The attempted bribe was made by a 27-year old Russain operative Egor Igorevich who is being charged by the justice department. His plan was simple, bribe an employee to install the malware, hold company data hostage in exchange for a several million-dollar payday.
The attempted attack further reveals a growing trend in cybercrime. These “insider threat” attacks circumvent the need to hack into a network by using bribes instead. For cybercriminals, success breeds success. The ransom received from a prior victim, such as the reported $10 million from Garmin, can quickly be turned around as a bribe to attack the next target. Companies going through an attack are very willing to pay the ransom to avoid the inconvenience, lost revenue or even reputation damage caused by downtime. Many companies who pay the ransom never make the attack known to the public or authorities. Garmin has yet to officially release details of their attack beyond acknowledging it occurred.
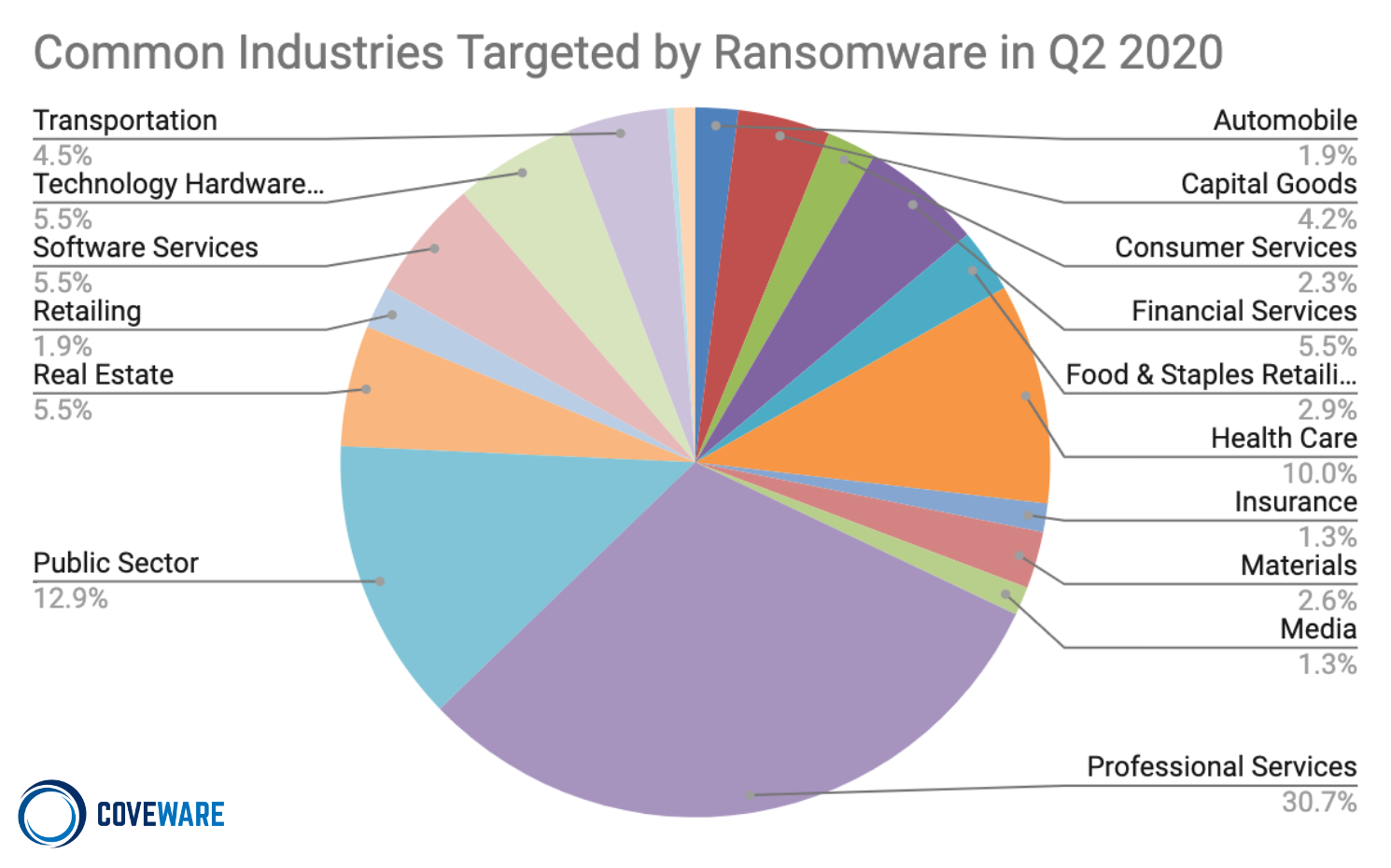
Primary targets of the recent malware attacks include larger corporations, professional service firms, healthcare and local governments — anyone who can’t afford downtime and has significant financial resources. The average downtime in Q2 2020 was 16 days, however; the total time to full recovery is generally measured in months.
With the rise of easily available Ransomware as a Service (RaaS), new small attack groups are forming and the cost of entry is extremely low. Threat groups no longer require deep technical expertise to carry out an attack and the impact of idle hands through unemployment and work-from-home could drive financially stressed individuals to cybercrime. Coveware, the Ransomware Recovery First Responders, report the average ransomware payment in Q2 2020 was $178,254 –marking a 60% increase over Q1 2020. Payment size has been steadily increasing since 2018 as attackers perform more targeted attacks on “big game” who can afford to pay as opposed to prior “spray and pray” techniques hitting mostly smaller targets.
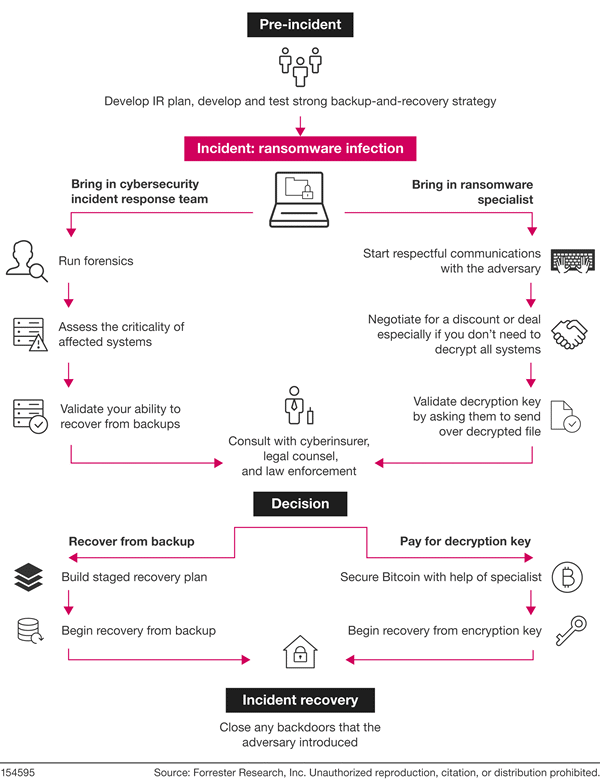
Forester Research reports that companies are increasingly opting to pay the ransom when attacked. Whether you decide to pay or not, will depend on the nature of the attack and your response plan. The more preparation you do before the attack, the stronger your positions will be if one occurs. Work with your managed service provider to ensure your business is ready should you be the next victim. An example Ransomware Incidence Response Workflow is provided below. Create a plan today because once your data is encrypted by attackers and your business grinds to a halt, it’ll be too late.