Cybersecurity Risk Assessment
There is no escaping the reality that we live in a world of geopolitical tensions and increasing threats from cyberattacks. Just last week the FBI issued a Liason Information Report (LIR) warning of a deteriorating security situation in Eastern Europe and the threat it imposes on the private sector in the U.S.
“The FBI Cyber Division, in coordination with the FBI’s Office of Private Sector (OPS), prepared this LIR to inform the private sector about the threat of Russian state-sponsored advanced persistent threat (APT) cyber activities, while tensions with Russia are heightened,”
The FBI report said such Russian APT actors “have used spear-phishing and brute force cyber network attacks (CNA), while exploiting known vulnerabilities against accounts and networks with weak security.” And as WatchGuard reports, zero-day attacks are increasing and now comprise over 67% of all attacks.
We know corporate networks are under increasing threat of zero-day, APT, and phishing attacks. The good news is we also know what to do about it. These times of heightened awareness are the perfect time to assess your organizations cybersecurity risk profile. And assessing your risk scenarios before an attack happens can greatly enhance deployments by adding clearly collected facts and analysis to response decisions.
A cybersecurity risk assessment is a process of identifying, estimating, and prioritizing information security risks. The risk assessment covers everything from policies, processes, employee training, and technologies used to protect an organization’s users and data. Cybersecurity risk assessments often leverage third-party cybersecurity frameworks, compliance, or regulatory standards to compare an organization’s security controls and posture against time-tested industry standards and best practices. The assessment serves as the launching point for an organization to better understand its current state of security and areas for improvement.
In creating your risk assessment, you will want to consider these common business use cases.
- On-site: Are your employees accessing company data and platforms from the office?
- Remote home office: Do you have a lot of employees working from home?
- Remote coffee shop, shared office: Do you expect your remote employees to access company networks from locations such as coffee shops?
- Traveling users: Do you have employees who travel and may access work platforms while on the go?
- Vertical: Is the service your company offers associated with specific business hours? For example, healthcare offices
- Third-party providers: Do you provide corporate network access to contractors or third-party providers?
- Device: Do you expect employees to access work information using their own devices?
Cybersecurity risk assessments involve three essential elements: a network assessment, a security assessment, and a vulnerability assessment.

Elements of cybersecurity risk assessment
As part of your risk assessment, you will want to better understand your digital assets and resources. Visibility in these areas can lead to risk mitigation outcomes such as micro-segmentation and a zero-trust environment.
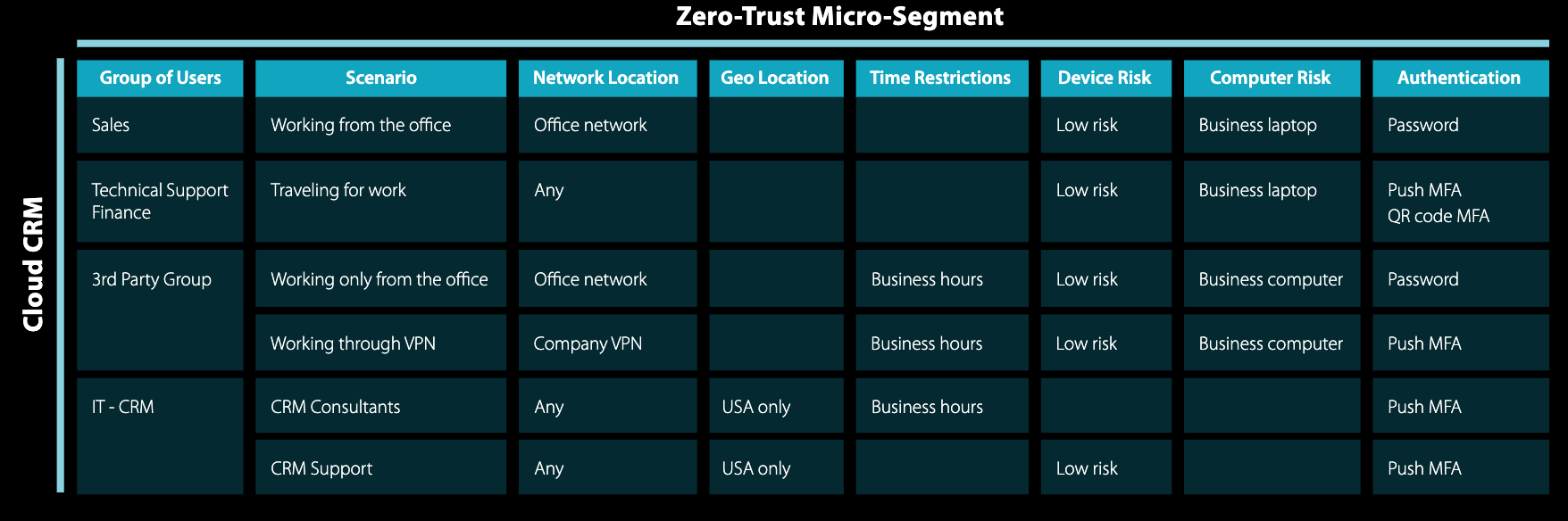
Example micro-segmentation template courtesy WatchGuard
The results of the risk assessment and network segmentation can then lead to informed risk-based authentication which can improve security and usability.
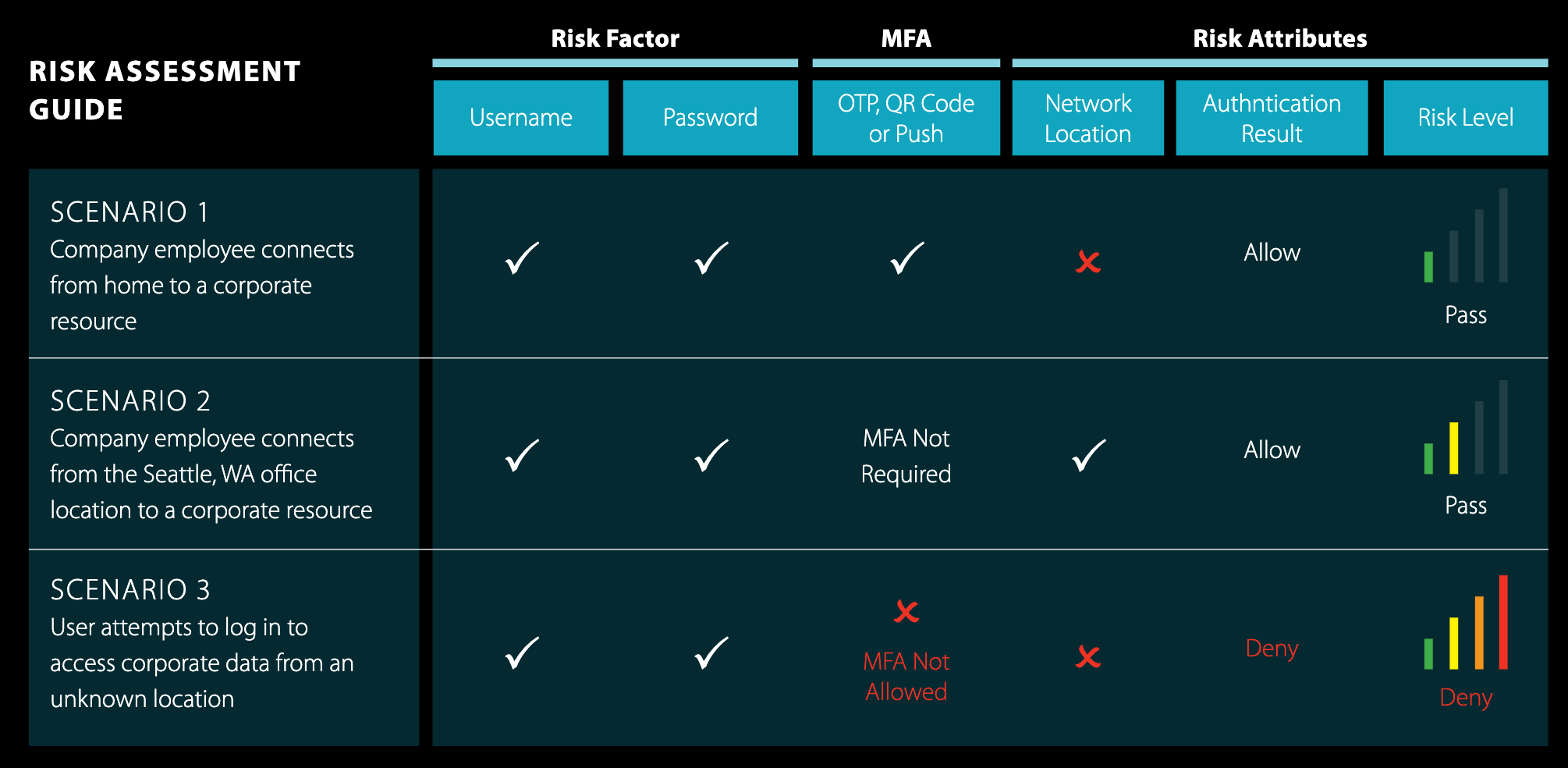
Example Risk Assessment Outcomes
If you are ready to better understand your organization’s current state of security and create a plan to mitigate risk and maintain business continuity in the face of any disruption, contact us. We have the tools and expertise to help.


![CISA Phishing Protection Recommendations [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph3ey82v3yws1xhe3qrjzci23y2f2zeozbzixdu.png)
