Insider Threats Represent 20% of Breaches
According to new data from Verizon in their 2022 Data Breach Incident Report, 20% of data breaches involved an actor internal to the organization. This represents a slight rise from 18% reported in the original Verizon DBIR back in 2008. While attacks are far more likely (80%) to result from external actors, insider attacks can result in 10x the amount of data stolen in a breach according to Verizon.
Examples of an insider as defined by the Cybersecurity & Infrastructure Security Agency (CISA) may include:
- A person the organization trusts, including employees, organization members, and those to whom the organization has given sensitive information and access.
- A person given a badge or access device identifying them as someone with regular or continuous access (e.g., an employee or member of an organization, a contractor, a vendor, a custodian, or a repair person).
- A person to whom the organization has supplied a computer and/or network access.
- A person who develops the organization’s products and services; this group includes those who know the secrets of the products that provide value to the organization.
- A person who is knowledgeable about the organization’s fundamentals, including pricing, costs, and organizational strengths and weaknesses.
- A person who is knowledgeable about the organization’s business strategy and goals, entrusted with future plans, or the means to sustain the organization and provide for the welfare of its people.
- In the context of government functions, the insider can be a person with access to protected information, which, if compromised, could cause damage to national security and public safety.
The impact from internal attacks scales by an order of magnitude compared to external attacks due to the privilege level of internal users and insider knowledge of data and systems. Insider threats often know exactly where the most valuable information is stored and know how to access it. Insiders can also often cover their tracks better and stay undiscovered longer allowing them time to scale the attack as an advanced persistent threat. Insider threats stem not only from employees of an organization but also 3rd party vendors and partners. Verizon’s original data from 2008 included partners representing 39% of all breaches and the Partner category currently represents 60% of incidents which is the third largest attack vector in their 2022 data.
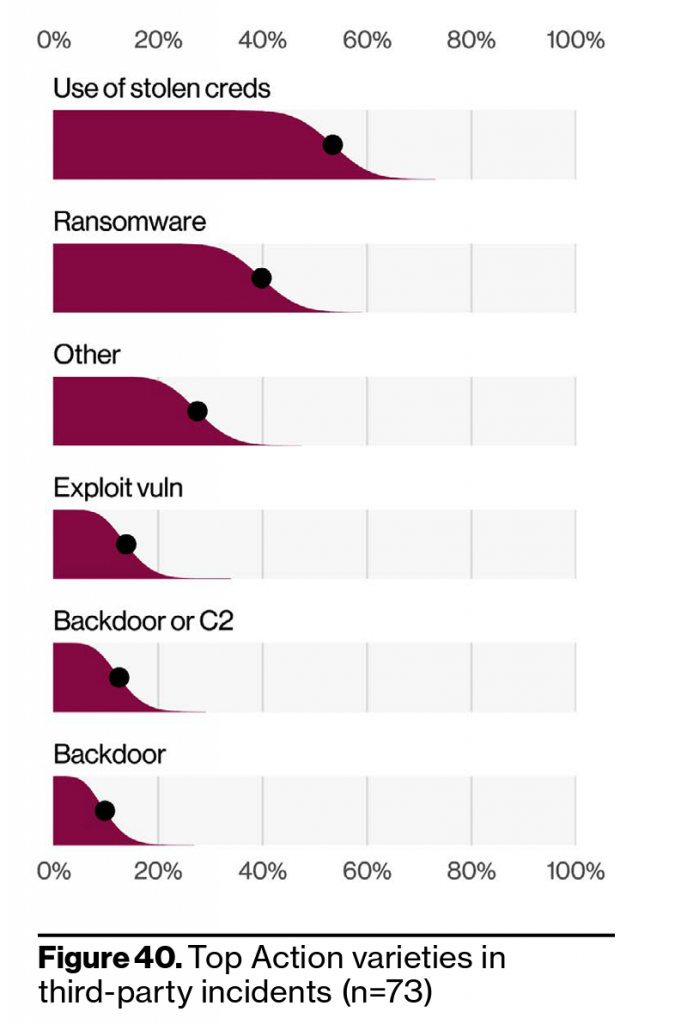
The sharp increase of breaches within the partner attack vector was the result of large supply chain attacks spreading through software updates. When you think of partners, are you considering your software vendors? If not, you could be missing one of the largest gateways to your data. Within these 3rd party breaches, stolen credentials and ransomware represented the top threat action varieties.
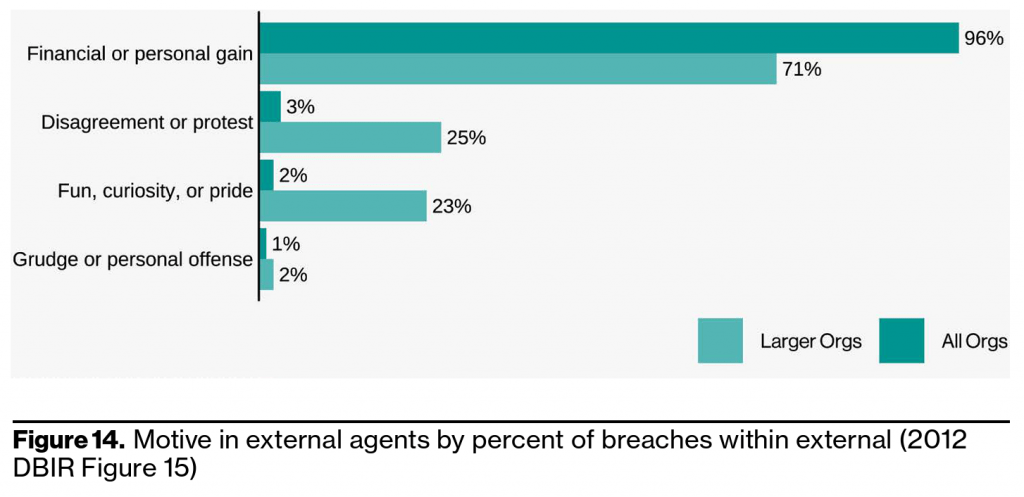
Motives for insider attacks are generally financials in nature but “getting even” or “protest” is significant, especially in larger organizations. Politically based attacks may not be as common as financially motivated attacks but they do attract national headlines and widespread attention — especially when they are state-sponsored. Frustrated, curious, and or bored insiders are also represented in the dataset in almost negligible size across all organizations.
Identifying insider threats to security and defending against insider threats can be challenging but starts with zero-trust security along with threat detection and response. Contact us to ensure you are protected.


![CISA Phishing Protection Recommendations [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph3ey82v3yws1xhe3qrjzci23y2f2zeozbzixdu.png)
