Security Tools Essential to Stop Insider Threats
According to the 2022 State of Remote Work Survey published by Pulse, 47% of respondents would prefer a mostly or completely remote work arrangement for their team. The results from the Pulse survey shouldn’t be surprising, we’ve seen the shift to remote work progress rapidly for over two years now. And now it seems some form of remote work is here to stay for nearly every office environment. According to Pulse, only 8% of remote employees are willing to return full-time to work after the pandemic. While 48% of workers want to work from home permanently, and the remaining 44% want to work from home for part of the week.
Insider threats to security are not a new concern, but the challenges insider threats present have been magnified through the dramatic shift to remote work. Along with the “work from anywhere” movement, another major shift is underway which is fueling the insider threat to security. At the same time as we accept the reality of increasing remote work, organizations are growing increasingly reliant on the digital transformation. According to Statista, the amount of data captured, copied, and consumed is expected to grow to more than 180 zettabytes through 2025. If a zettabyte is hard to grasp, the parabolic trend in the below graph should simplify comprehension of the digital storage growth we are witnessing. In the next three years, our total data and information stored will double.
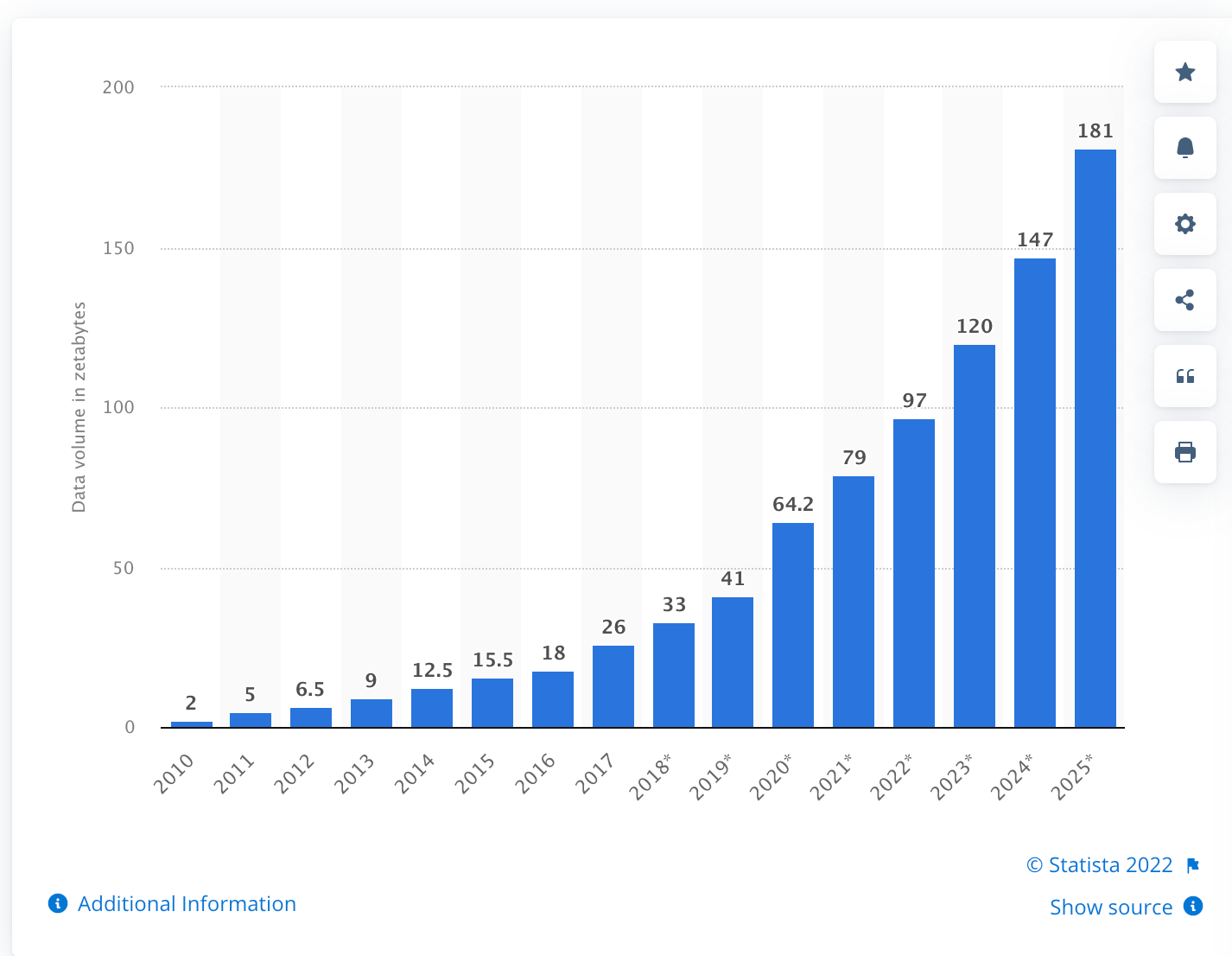
This confluence of remote access to information that enables work from anywhere and the digitization of everything has elevated the risk presented by insider threats. Malicious attacks or even inadvertent leaks can hit at any time and from any location and now they potentially have access to far more information.
In a new survey published by Microsoft on Building a Holistic Insider Risk Management Program, two-thirds of respondents stated that “Data theft or data destruction from departing employees is a form of insider risk that is becoming more commonplace.”
According to Verizon’s DBIR, financial gain represents the largest motivator for intentional insider attacks; however, according to Microsoft, the greatest impact witnessed by the victim organization from the attacks is the loss of data. To the victim organization, the data lost represents the largest impact on business even though the average single-event incident cost exceeded $500,000.
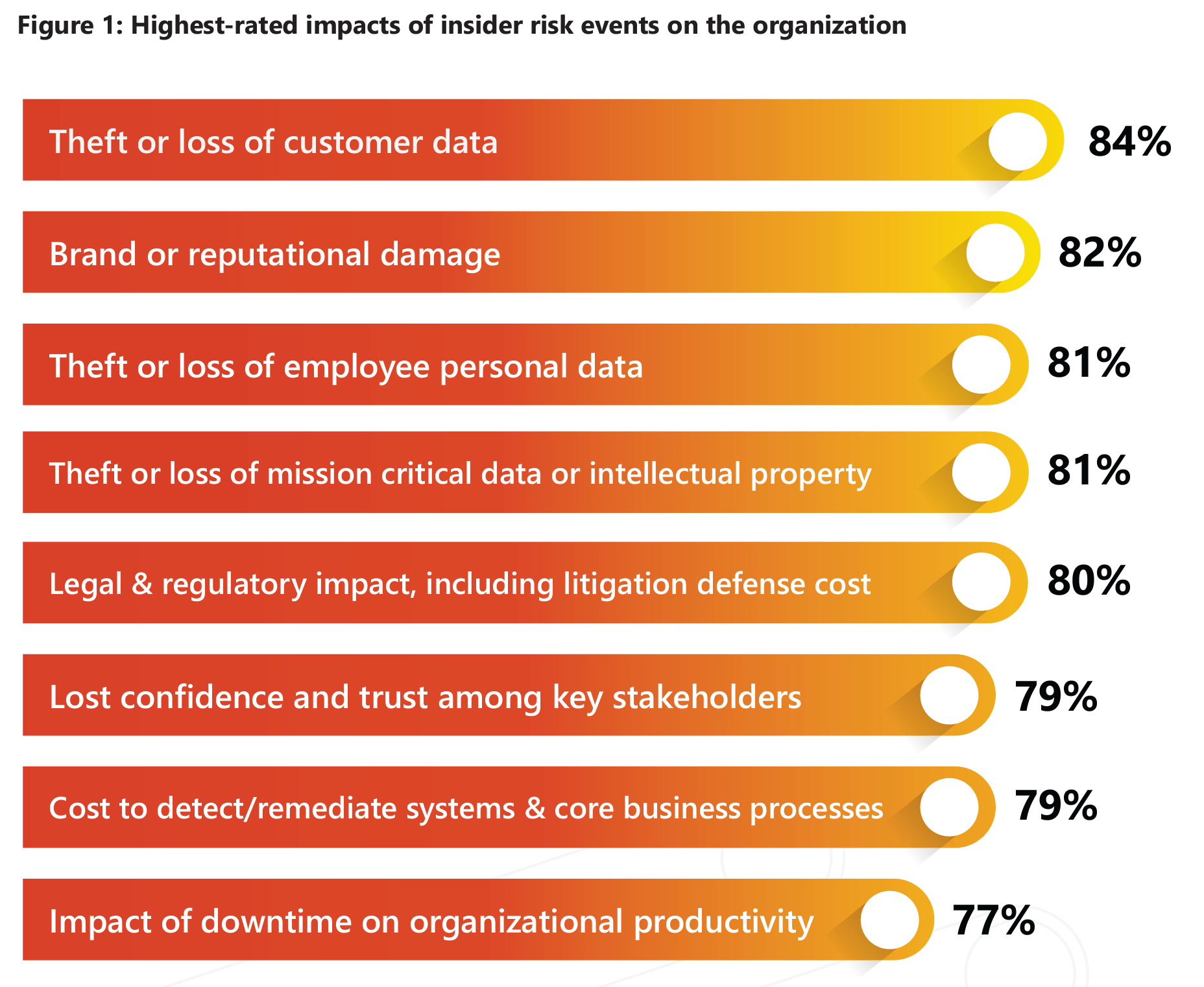
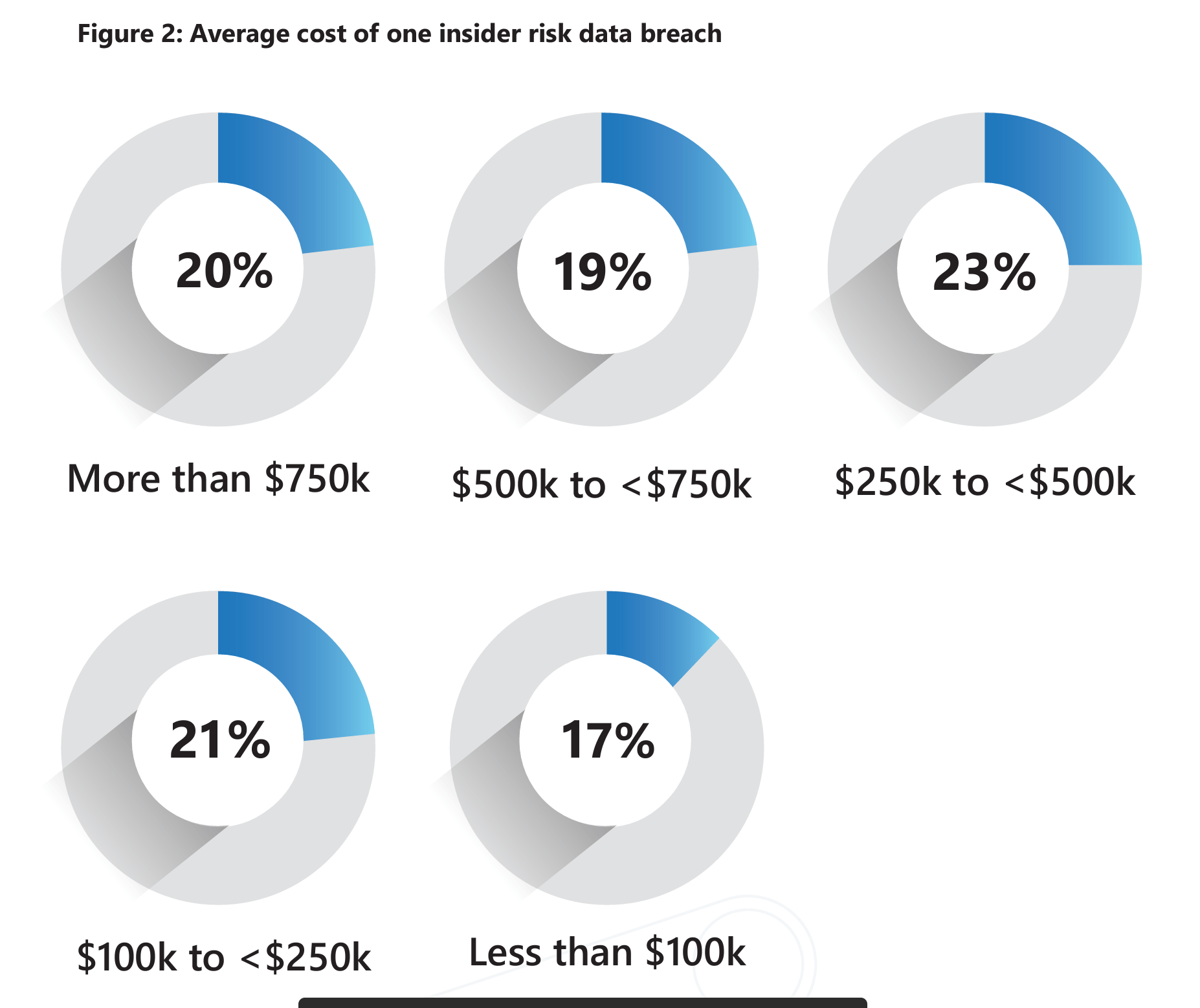
So we know the world is becoming exponentially more digital, remote work is likely here to stay in one form or another and this creates an opportunity for increasing insider attacks. How do we mitigate the likelihood of these attacks? Fortunately, beyond corporate buy-in and continued employee education around insider threats, many of the security tools essential to general IT security are also key components in defending against insider threats.
- Extended Detection and Response (XDR)
- Network Detection and Response (NDR)
- Privileged Access Management (PAM)
- User Activity Monitoring (UAM)
- Incident Threat Management (ITM)
- Endpoint Detection and Response (EDR)
- Security and Information Event Management (SIEM)
- User and Entity Behavioral Analysis (UBA/UEBA)
Detecting insider attacks remains a challenge for security teams as insiders often know exactly how to elude security. Combining increased usage of the above tools based on risk factors and triggering events can lead to earlier detection. Triggering events can mean identifying when specific users take specific actions, for instance when an organizational leader accesses, downloads, or exfiltrates particularly sensitive files, such as confidential IP or revenue forecasts. Risk factors that may also lead to increased tool utilization include:
- Usage of devices owned or managed by the company
- Seniority in the org chart
- Having completed specific training
- Resignation notice
- Access rights to high-risk data
- High-risk job roles
- Current/prior threatening behavior
- New hire probationary period
- Duration of involvement in high-risk projects
Of course, no tools or risk factors can match the impact of creating and reinforcing a positive work environment where disgruntled and angry employees are the exception. Fostering an environment that builds a mutually beneficial team environment between leadership, employees, and the corporate mission is essential to reducing attacks. However, no organization is perfect and all attack motivations can’t be eliminated. This is why establishing the proper tools, policies, and protocols to mitigate risks and detect threats is essential to any insider risk management program. Contact us to ensure your data is safe.



