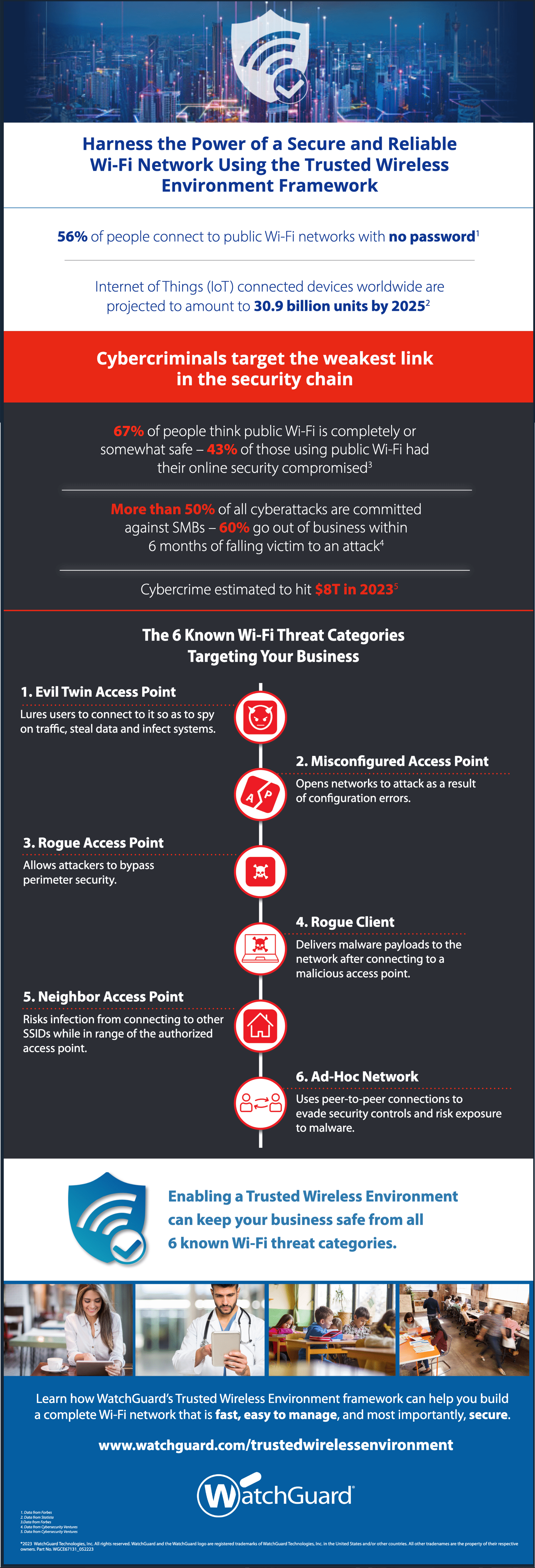
The 6 Known Wi-Fi Threat Categories [Infographic]
Our friends at WatchGuard have published a new infographic detailing the six known Wi-Fi threat categories. We’ve detailed the six threats below and you can read more in our Wi-Fi Security Trends series and Wi-Fi 6 Upgrade Guide.
Evil Twin Access Point: Imagine this: You walk into a coffee shop, and you see two Wi-Fi networks with almost the same name—one is the legitimate network, and the other is an imposter. That imposter is the Evil Twin Access Point. It tricks people into connecting, thinking it’s the real deal. But once connected, the attacker running the Evil Twin can steal your login details, credit card info, or any other sensitive data you send over that network. So be cautious when connecting to Wi-Fi in public places!
Access Point Misconfigurations: Misconfigurations can be like leaving your front door unlocked or forgetting to set the alarm. When setting up a Wi-Fi network, some people might use weak passwords, outdated security settings, or forget to update their Wi-Fi router’s firmware. Hackers love to find these misconfigured networks, as they can easily break in and snoop around. They might access your personal files, use your internet connection for illegal activities, or even launch attacks on other devices connected to your network.
Rogue Access Point: You’re working at your office, and suddenly, you see an unexpected Wi-Fi network available. That’s a Rogue Access Point! It’s a sneaky little network set up by an unauthorized person, and it can cause real trouble. They might use it to get into your company’s internal network, steal sensitive data, or monitor your online activities. So, if you spot an unknown Wi-Fi network in your workplace, report it immediately to your IT department.
Rogue Client: Think of a Rogue Client as an unwelcome guest crashing a party. It’s a device that connects to your Wi-Fi network without permission. This could be someone’s phone, laptop, or any other device. The problem is, it might be infected with malware or trying to do something shady. It can mess up your network, slow down your internet, or even steal data from other connected devices.
Neighbor Access Point: Imagine living in an apartment building, and your neighbor sets up a Wi-Fi network. If they don’t secure it properly, you might be able to see and connect to their network. That’s a Neighbor Access Point. While it may seem convenient to use their Wi-Fi, remember that they can see your internet traffic, and if someone else is snooping around their network, they might see your data too! Always stick to your own secured network to be safe.
Ad-hoc Network: An Ad-hoc Network is like having a direct, one-on-one chat with someone without going through a mediator. It’s when two devices directly connect to each other without using a Wi-Fi router. While this can be handy for sharing files with a friend, it can be risky in public places. Let’s say you enable an Ad-hoc connection at a coffee shop; a hacker nearby might use this opportunity to intercept your data or even send you malware.
So, in a nutshell, when dealing with Wi-Fi, always be cautious, use secure connections, and be aware of any suspicious networks or devices around you! And let the pros secure your network.

![The 6 Known Wi-Fi Threat Categories [Infographic] The 6 Known Wi-Fi Threat Categories [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph35udri0x8hmgbnjva9jb2z042bi02c6bmt588.png)

