The Need For Managed Infrastructure Security Services
It is widely believed that the next great war will not be fought on the battlefield. Instead, it will be fought through currency wars and cyber attacks. Just this month the Federal Depository Library Program program’s website was defaced in a hacking and immediately taken offline.
In a statement after the attack, the Department of Homeland Security warned:
“Iran maintains a robust cyberprogram and can execute cyberattacks against the United States, Iran is capable, at a minimum, of carrying out attacks with temporary disruptive effects against critical infrastructure in the United States.”
The DHS goes on to say:
“In these times of increased threats all organizations should increase cyber monitoring, back up IT systems, implement secure authentication and have an incident response plan ready should a hack take place.”
Cyberwarfare is not new but the threats it presents are rapidly growing as we increasingly rely on networked computer systems for accessing critical information, managing business processes and performing financial transactions. As Jean-Luc Vez, the World Economic Forum’s Head of Security puts it:
“The digitization of society has created progress and empowerment. But it also has a dark side: cybercrime and cyber warfare.”
The number of cybersecurity incidents around the globe continues to increase at an increasingly rapid pace year over year.
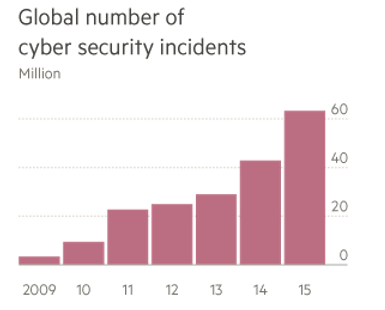
Image: Financial Times, Check Point, PwC
And the average costs of resolving the cybercrimes are significant.
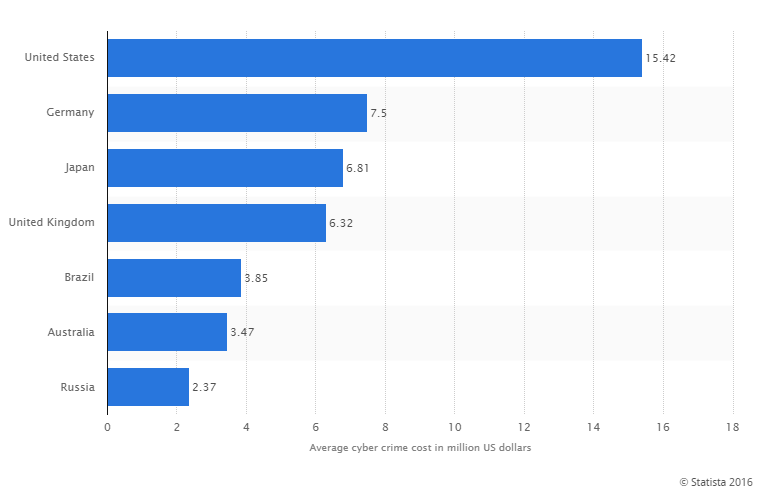
Image: Statista
As we have explored previously, your business doesn’t have to be a government agency or a holder of sensitive data to be a target. Instead, having server and network resources available and not hardening those resources to protect against the latest threats makes your network a target. Hackers will gain access to your network simply to use your resources in mounting a larger attack on a high-profile target. Using this model of attacking the weakest in the herd, hackers can increasingly leverage previously hacked resources to gain further reach in attacking more vulnerable assets. It is a snowball effect that allows the hackers to become very efficient at leveraging an incredible scale of computing power to repeatedly test every computer system for the latest vulnerabilities and continue building their own network of compromised resources. If you don’t take network infrastructure seriously, chances are you may already be compromised and you don’t even know it.
Network Infrastructure Security takes a proactive approach to assessing and creating a plan to harden your network through:
- Penetration Testing
- Security Assessments
- Vulnerability Assessments
- Piranha (Phishing Simulation)
- Security Training and Awareness
Managed Network Infrastructure Security takes preventive measures a step further into actual implementation, management and ongoing system evolution. Establishing a management cycle essentially closes the loop between the assumptions made in the initial assessments and real-world data on the types of attacks your network is currently facing.
- Do you have a network infrastructure team established?
- Have you modeled your system?
- Have you considered risks and mitigations?
- Do you have a risk plan and identified risk owners?
- Are you continuously monitoring your network infrastructure and adapting as needed?
At Verus we take Managed Network Infrastructure seriously. We live and breathe network threats so that our clients can rest assured they are leading the herd and not falling behind to become the prey.



