Threat Hunting and the Tools for Advanced Endpoint Security
Threat hunting is an analyst-based process allowing organizations to discover hidden, and advanced threats that go undetected by automated detection and prevention controls. In simple terms, the threat hunting mission is to find those unknown threats that manage to bypass technology-based controls. Threat hunting is an emerging discipline and due to the current threat landscape, is becoming an essential component of any cybersecurity program.
Organizations are adding threat hunting to their security programs at an increasing rate because as we’ve seen in the past year, advanced persistent threats, fileless malware, and zero-day exploits can evade automated security tools.
According to WatchGuard’s Q4 2020 Internet Security Insights Report, fileless malware attacks rose 888% in 2020 over the prior year. The data is quantifiable and based on a year’s worth of endpoint threat intelligence collected from WatchGuard Panda products. Fileless malware, also known as “living off the land” malware, are threats that don’t enter a network through a traditional file. This means the malware is never written to disk and generally remains unnoticed by anti-virus scans. Because the attacks don’t bring resources or tools with them, they can remain undetected unless advanced endpoint protections such as threat hunting are employed.
Advanced Persistent Threats (APT) are another growing attack better defended against through threat hunting. An example of an APT is the recent SolarWinds attack. In the incident, attackers were able to remain within the SolarWinds networks for over 12 months without being detected. This level of detection avoidance is common in APT attacks where the adversary has high levels of expertise and significant resources dedicated to establishing a foothold. APTs can use multiple attack vectors (e.g., cyber, physical, and deception) to generate opportunities and achieve their objectives. APTs are able to adapt to a defender’s efforts to resist it and maintain the level of interaction needed to execute its objectives.
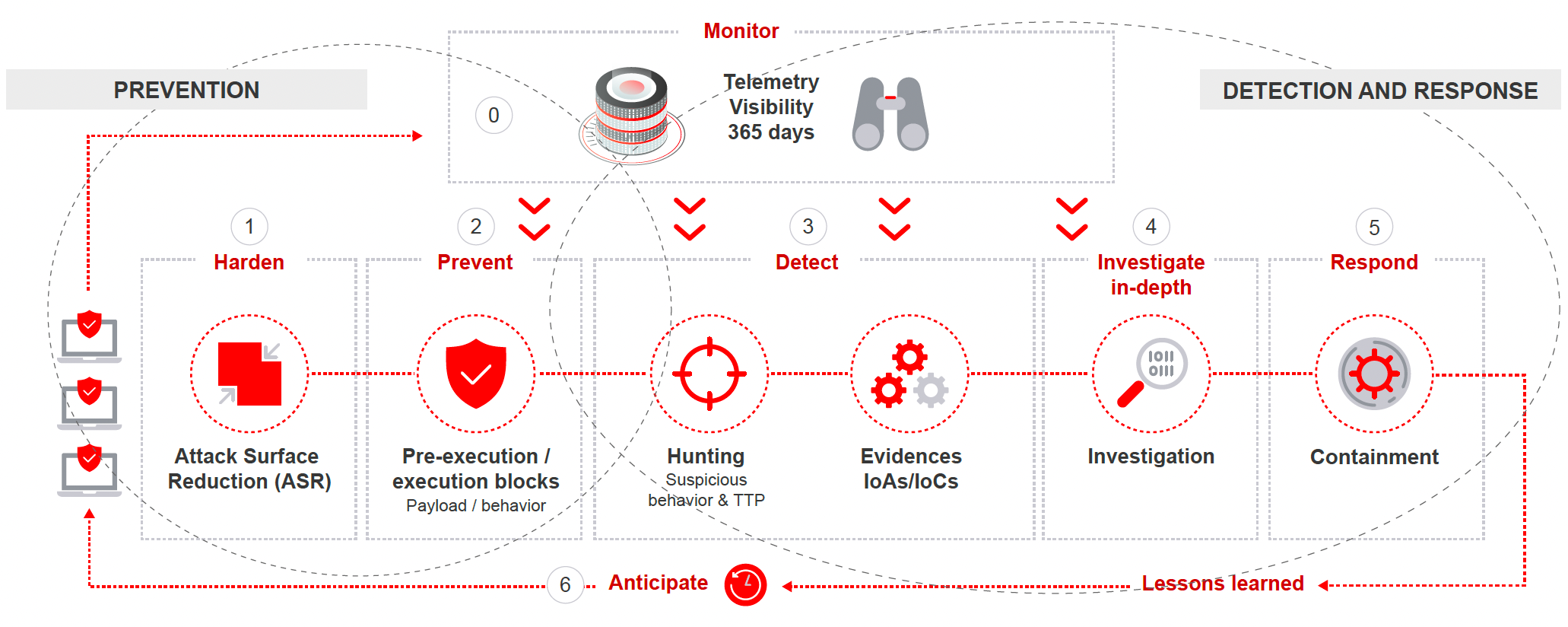
Threat hunting can identify these advanced threats through data analysis by adding a human element to the security process. Skilled IT security professionals search for and monitor threats before they cause serious problems. Threat hunting, when executed in real-time, can significantly reduce threat identification and response times.
Threat hunting is a function that works in parallel with automated security workflows. Its core function is to extract insights from telemetry to automate new deterministic analytics. Additionally, threat hunting also comprises the combined activity of applying these new analytics to the telemetry and contextualizing weak signals to streamline the identification of actual attacks.
According to Pulse, 32% of IT leaders say that their organizations plan to reinforce their endpoint security posture by adding a threat hunting program to their overall security strategy.

The key values threat hunting provides to a security program are:
- Allows for the timely discovery and disruption of internal and external threats that have bypassed technology-based controls before a breach.
- Augments security technologies with human expertise to reduce the dwell time.
- Arms security teams with insights required to disrupt adversaries at scale
- Feeds the continuous effort of reducing the attack surface and improving automated detection capabilities.
Implementing threat hunting does require allocation of human expertise dedicated to the task, structured workflows within the security program, and visibility of telemetry across all devices. Due to these hurdles, many organizations outsource threat hunting to established teams such as WatchGuard’s threat hunting service through WatchGuard Advanced Endpoint Security. Through outsourcing, organizations gain elite-level expertise in threat hunting and extend the existing security team capabilities. Contact us to start down the path of better security through advanced protections such as threat hunting.


![CISA Phishing Protection Recommendations [Infographic]](https://veruscorp.com/wp-content/uploads/bfi_thumb/dummy-transparent-ncnph3ey82v3yws1xhe3qrjzci23y2f2zeozbzixdu.png)
