What is a Cloud Firewall or Firewall as a Service (FWaaS)?
Firewalls are a critical component in today’s network security. While most of us are familiar with the next-generation firewalls that physically reside in server racks providing a hardware and software barrier to outside networks, cloud-based firewalls form a virtual barrier around cloud platforms, infrastructure, and applications.
Businesses are migrating to the cloud for seamless scalability, increased effectiveness, faster implementation, mobility, and disaster recovery. Managed service providers are evolving with the cloud as they adapt to and implement cloud security strategies in a multi-cloud world. In fact, cloud migration services market was valued at $119.13 billion in 2020 and is expected to reach $448.34 billion by 2026. That is a compound annual growth rate (CAGR) of 28.89% over the forecast period 2021 – 2026 according to data from Mordor Intelligence. Cloud adoption by corporations of all sizes is accelerating and remains a significant consideration for IT cost reduction, accessibility, and security strategies.
With the rapid transition and integration of cloud services into corporate IT stacks, cloud-based firewalls filter out potentially malicious network traffic — just like a traditional firewall. Cloud-based firewalls, also known as firewall as a service (FWaaS), can block malicious traffic, including malware and bots, from accessing cloud resources and they can also protect from allowing sensitive data to leave. FWaaS eliminates traditional firewall choke points as they are cloud-based and don’t rely on all data passing through any single point for processing. And just like other cloud services such as SaaS and IaaS, FWaaS can instantly scale up to handle more traffic.
FWaaS solutions are cloud vendor specific. This means there isn’t a one-size-fits-all firewall solution. Fortunately, if your cloud resources reside in the largest or most common cloud environments such as Amazon Web Services (AWS) and Microsoft Azure, there are FWaaS solutions such as WatchGuard Firebox cloud that cover both providers.
The public cloud provides countless new opportunities for businesses big and small; its continued growth has also made it a major focus for criminal hackers. Hackers have begun to target or infect servers running in public cloud services, and there have even been cases where hackers have taken over servers running in Amazon EC2 – the virtualized compute portion of AWS. From a security perspective the servers you spin up in public cloud environments, like Azure or AWS, are no different than those in your own data center. If you leave a port open, without a firewall or access control rules, hackers can attack it in the same way they attack physical servers.
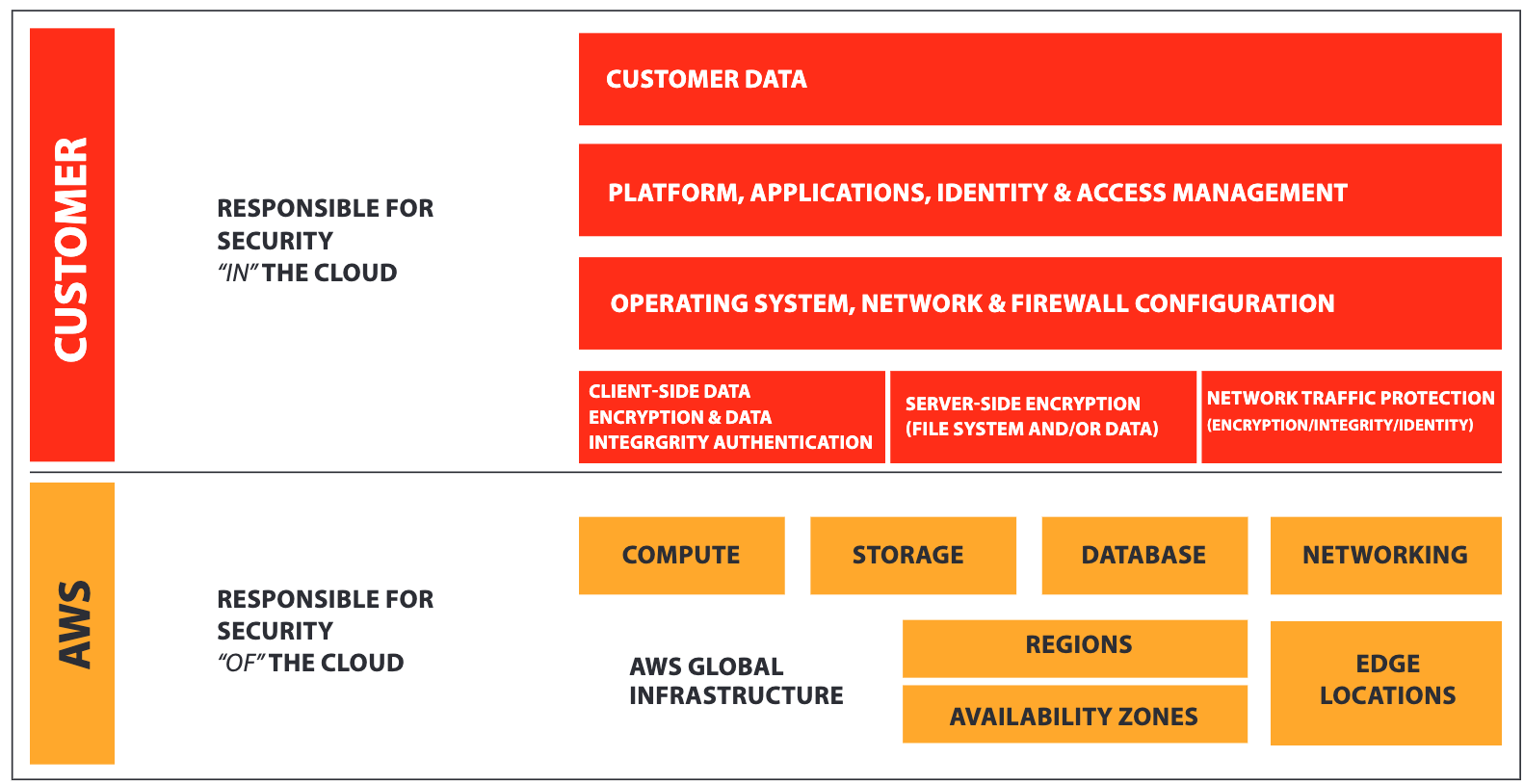
Cloud vendors such as AWS and Azure take pride in the security of their cloud infrastructure, but they make it clear that the security of your business-critical assets in the cloud is your responsibility. An example under the AWS Shared Responsibility Model, AWS makes a distinction between:
- Security measures that the cloud service provider (AWS) implements and operates – “security OF the cloud”
- Security measures that the customer implements and operates, related to the security of customer content and applications that make use of AWS services – “security IN the cloud”
In essence, AWS manages the security OF their cloud through a series of security tools that protect their endpoints, provide encryption of stored data, and effectively segregate the virtual networks and applications of their customers. Under the shared responsibility model, you remain in control of the security approach to your content, platform, applications, and networks.